F5 Waf Configuration Guide
Guided Configuration for Advanced Web Application Firewall The Guided Configuration 50 release includes A new REST API Security (Open API Spec) configuration template for API Security (previously known as API Protection) use case The configuration allows you to import an OpenAPI Specification (formerly called Swagger version ) and set up the BIGIP Advanced Web Application Firewall.

F5 waf configuration guide. F5 BIGIP hardwarerelated confirmation command;. Configuring your App Service Environment To configure an App Service Environment, refer to our documentation on the subject Once you have an App Service Environment created, you can create Web Apps, API Apps, and Mobile Apps in this environment that will all be protected behind the WAF we configure in the next section Configuring your Barracuda WAF Cloud Service. 228 Task 7 – Demonstrate F5 WAF blocking functionality;.
F5 BIGIP WAF Declarative Policy WAF specific configurations on a BIGIP system by using a declarative policy model. ELK based dashboards for F5 WAFs This is community supported repo providing ELK based dashboards for F5 WAFs How does it work?. This topic describes preliminary steps, such as creating an AWS account, to prepare you to use AWS WAF, AWS Firewall Manager, and AWS Shield Advanced You are not charged to set up this account and other preliminary items You are charged only for AWS services that you use.
F5 Networks Threat Research Team has created a tool that provides an easy and fast way to integrate security testing as part of the SDLC process for basic application protection health check before moving to production The tool is intended to test the WAF configuration state and its provided. F5 Advanced WAF management interface is now webbased and purposebuilt for security practitioners so the policy configuration, logging, alerting, violation severity and analysis are all there as. Before you proceed with the initial setup, choose the deployment mode under Operation Mode (Proxy or Bridge All) in the BASIC > IP Configuration page Choose your deployment mode based on your current network configuration and the types of services you want from the Barracuda Web Application Firewall.
Before you proceed with the initial setup, choose the deployment mode under Operation Mode (Proxy or Bridge All) in the BASIC > IP Configuration page Choose your deployment mode based on your current network configuration and the types of services you want from the Barracuda Web Application Firewall. F5 BigIP ASM introduction 1 1 BIGIP ASM Comprehensive Application SecurityPresenter 2 2Attacks are Moving “Up the Stack” Network Threats Application Threats 90% of security 75% of attacks focused investment focused here here Source Gartner. Configuration Summary The following links provide instruction on how to integrate F5 BIGIP APM with RSA SecurID Access This document is not intended to suggest optimum installations or configurations It assumes the reader has both working knowledge of all products involved, and the ability to perform the tasks outlined in this section.
What is a Web Application Firewall?. 225 Task 4 – Accept EULA for F5 WAF in Azure Marketplace;. The configuration object from step 2 is a copy of the waf_service object in the Essential App Protect schema from the state of your service instance at that time In order to roll back to that state, simply change the waf_service object in the payload for the update subscription request to the configuration object you saved in step 2, as shown.
Web application firewall mod_security installation and configuration how to protect attack on web server by using mod_security WAF is work on session WAF. To prevent the system from importing the configuration during the upgrade process, refer to K Controlling configuration import when performing software installations Impact of procedure If the BIGIP system serves high volume traffic, F5 recommends that you perform the entire upgrade during a maintenance window, to lessen the impact on. F5 BIGIP network related commands;.
Testing the configuration Viewing reports for antivirus detection Limitations Using F5's Web Application Firewall solution together with MetaDefender ICAP Server will help you prevent malware reaching your web application by analyzing files being uploaded with all of the engines in MetaDefender Core. LTM Node Operation Command in F5 BIGIP;. F5 Networks Configuring BIGIP Advanced WAF Web Application Firewall COURSE OVERVIEW In this 4day course, students are provided with a functional understanding of how to deploy, tune, and operate F5 Advanced Web Application Firewall to protect their web applications from HTTPbased attacks The course includes.
F5 frequently updates the operations guides and new guides may be released as needed If you would like to be notified when new or updated content is available, or if you have feedback, corrections, or suggestions to improve this guide, email opsguide@f5com F5 internal users can file a request using ServiceNow Configuration utility. This Quick Start deploys a BIGIP Virtual Edition (VE) cluster on the Amazon Web Services (AWS) Cloud in about 30 minutes BIGIP VE is an application delivery and security services platform from F5 Networks that provides speed, availability, and security for businesscritical applications and networks. This article describes how to back up and restore your BIGIP 11x through 16x configuration data using a UCS configuration archive The UCS archive, by default, contains all of the files you need to restore your current configuration to a new system, including configuration files, the product license, local user accounts, and SSL certificate/key pairs.
Testing the configuration Viewing reports for antivirus detection Limitations Using F5's Web Application Firewall solution together with MetaDefender ICAP Server will help you prevent malware reaching your web application by analyzing files being uploaded with all of the engines in MetaDefender Core. 225 Task 4 – Accept EULA for F5 WAF in Azure Marketplace;. How to configure a simple policy using the F5 APM.
Contents 1 Getting Started;. Installing the Data Gathering Agent F5IsHandlerdll on an IIS 70 server Installing the Data Gathering Agent F5IsHandlerdll on an IIS 75 server Installing the Data Gathering Agent F5IsHandlerdll on an IIS 80 or 85 server. How F5's ASM/WAF can protect your public facing web sites.
May 16, 18 presentation during our sales operations support allhands team meeting about the new F5 Advanced Web Application Firewall. F5 BIGIP CLI Commands How to use F5 BIGIP Configuration Files;. F5 Advanced WAF management interface is now webbased and purposebuilt for security practitioners so the policy configuration, logging, alerting, violation severity and analysis are all there as.
A software or hardware solution that protects your web enabled applications from threats/attacks The solution must understand web protection at the application layer (HTTP and HTTPS conversations to your web applications, XML/SOAP, and Web Services) Detect/prevent OWASP Top Ten Threats. F5 discovers and investigates these attacks This feature requires a Threat Campaigns subscriptionbased service license Behavioral WAF (BIGIP 1500 and later) Provides new and updated content for Deception Response Pages Configuration of Deception Response Pages requires an Advanced WAF license. 228 Task 7 – Demonstrate F5 WAF blocking functionality;.
LTM Pool Operation Command in F5 BIGIP;. In this 4 day course, students are provided with a functional understanding of how to deploy, tune, and operate F5 Advanced Web Application Firewall to protect their web applications from HTTPbased attacks The course includes lecture, handson labs, and discussion about different F5 Advanced Web Application Firewall tools for detecting and. ELK stands for elasticsearch, logstash, and kibana Logstash receives logs from the F5 WAF, normalizes them and stores them in the elasticsearch index.
F5 BIGIP iRules Examples;. When server stress occurs, F5 Advanced WAF can rate limit or drop those source IP addresses whose behavior has exceeded the thresholds for legitimate traffic Behavioral DoS is fully automated and has no configuration other than the four modes of operation. Before you proceed with the initial setup, choose the deployment mode under Operation Mode (Proxy or Bridge All) in the BASIC > IP Configuration page Choose your deployment mode based on your current network configuration and the types of services you want from the Barracuda Web Application Firewall.
ELK stands for elasticsearch, logstash, and kibana Logstash receives logs from the F5 WAF, normalizes them and stores them in the elasticsearch index. Application Security Manager (ASM) This is F5’s Web Application Firewall (WAF), if you understand how traditional firewalls block and allow traffic by means of IP & Ports, you can think of the F5 ASM as filtering and protecting everything after the slash “/” in your URL – specifically on the contents of requests to your web application, including the URIs and posted parameters. Azure Web Application Firewall (WAF) on Azure Application Gateway provides centralized protection of your web applications from common exploits and vulnerabilities Web applications are increasingly targeted by malicious attacks that exploit commonly known vulnerabilities SQL injection and crosssite scripting are among the most common attacks.
227 Task 6 – Review F5 WAF Configurations and Policies;. 227 Task 6 – Review F5 WAF Configurations and Policies;. LTM Monitor Operation Command in F5 BIGIP;.
Welcome to the GitHub repository for F5's ARM templates for Azure deployments All of the templates in this repository have been developed by F5 Networks engineers This repository contains one main directory supported supported The supported directory contains our legacy Azure ARM templates that have been created and fully tested by F5 Networks. ELK based dashboards for F5 WAFs This is community supported repo providing ELK based dashboards for F5 WAFs How does it work?. F5 discovers and investigates these attacks This feature requires a Threat Campaigns subscriptionbased service license Behavioral WAF (BIGIP 1500 and later) Provides new and updated content for Deception Response Pages Configuration of Deception Response Pages requires an Advanced WAF license.
Thoroughly tested, stepbystep configuration procedures guide you through a fast, successful deployment with your applications EN EN;. Configuring your App Service Environment To configure an App Service Environment, refer to our documentation on the subject Once you have an App Service Environment created, you can create Web Apps, API Apps, and Mobile Apps in this environment that will all be protected behind the WAF we configure in the next section Configuring your Barracuda WAF Cloud Service. In this 4 day course, students are provided with a functional understanding of how to deploy, tune, and operate F5 Advanced Web Application Firewall to protect their web applications from HTTPbased attacks The course includes lecture, handson labs, and discussion about different F5 Advanced Web Application Firewall tools for detecting and.
In this 4 day course, students are provided with a functional understanding of how to deploy, tune, and operate F5 Advanced Web Application Firewall to protect their web applications from HTTPbased attacks The course includes lecture, handson labs, and discussion about different F5 Advanced Web Application Firewall tools for detecting and. The F5 Advanced Web Application Firewall (WAF) provides a powerful set of security features that will keep your Web Applications safe from attack Many WAFs. F5 Web Application Firewall Solutions > Class 6 AWAF in a CI/CD Pipeline > Module 2 Appendix A f5 WAF Tester Administrator Guide When going through the configuration file prompts (/f5waftester –init), there are more prompts that you can configure.
It's time to get your hands dirty!!!. 1 Beginning in BIGIP ASM 1210, for commaseparated values logging format, you can only limit the request and query string sizes when you select request and query_string in the storage format list Logging bots The BIGIP 130x system includes a new log option for reporting on bots After the option is enabled, results display on the ASM Reporting page. Indepth guide of web application firewalls, their benefits and weaknesses in 19 Depending on all sorts of configuration specifics, F5 Silverline WAF Process.
In this lab we will configure and test the Brute Force Mitigation features in F5 ASM to mitigate various Credential Stuffing attacks The purpose of this lab is to learn how and why ASM detects a given credential stuffing attack based on a given entity (username, IP address, or DeviceID) or a widely distributed attack. 229 Task 8 – Finalize the WAF Deployment;. Advanced Web Application Firewall (WAF) Protect your apps with behavioral analytics, proactive bot defense, and applicationlayer encryption of sensitive data Use the.
Getting Started with F5 Advanced WAF Guided Configuration. 226 Task 5 – Launch Azure Security Center and deploy the F5 WAF;. Consult the BIGIP Access Policy Manager Configuration Guide for more information about creating and modifying Access Policies or contact F5 support Navigate to Access Policy → Customization → Advanced and change the "Edit Mode" to Advanced Navigate through the Access Profiles tree to the Common folder beneath your Access Policy.
The F5 Advanced Web Application Firewall (WAF) provides a powerful set of security features that will keep your Web Applications safe from attack Many WAFs. Imperva WAF is a key component of a comprehensive Web Application and API Protection (WAAP) stack that secures from edge to database, so the traffic you receive is only the traffic you want We provide the best website protection in the industry – PCIcompliant, automated security that integrates analytics to go beyond OWASP Top 10 coverage, and reduces the risks created by thirdparty code. Here, the SecRemoteRules directive configures the NGINX ModSecurity WAF to download rules from the remote server, represented by the , using the provided The Wizard does not provide an interface for adding the directive, so you need to edit /etc/nginx/modsec/mainconf manually and add the SecRemoteRules directive presented by the Wizard (we created the mainconf file in.
Configure 1 Node2 Pool3 Poolmember4 Virtual Server. Application Security Manager (ASM) This is F5’s Web Application Firewall (WAF), if you understand how traditional firewalls block and allow traffic by means of IP & Ports, you can think of the F5 ASM as filtering and protecting everything after the slash “/” in your URL – specifically on the contents of requests to your web application, including the URIs and posted parameters. 229 Task 8 – Finalize the WAF Deployment;.
For initial installation, the BIGIP ® hardware includes a hardware setup guide for your platform that you can refer to for details about how to install the hardware in a rack, connect the cables, and run the setup utility Next, you must configure the BIGIP system on your network before you can use Application Security Manager™ (ASM) to create a security policy. Guided Configuration for Advanced Web Application Firewall The Guided Configuration 50 release includes A new REST API Security (Open API Spec) configuration template for API Security (previously known as API Protection) use case The configuration allows you to import an OpenAPI Specification (formerly called Swagger version ) and set up the BIGIP Advanced Web Application Firewall. Advanced WAF Advanced WAF › F5’s portfolio of automation, security, performance, and insight capabilities empowers our customers to create, secure, and operate adaptive applications that reduce.
The NGINX ModSecurity WAF protects web applications against SQL Injection (SQLi), Remote Code Execution (RCE), Local File Include (LFI), cross‑site scripting (XSS), and many other attacks This chapter explains how to install the NGINX ModSecurity WAF, presents a sample configuration of a simple rule, and sets up logging. F5 Networks Configuring BIGIP Advanced WAF Web Application Firewall COURSE OVERVIEW In this 4day course, students are provided with a functional understanding of how to deploy, tune, and operate F5 Advanced Web Application Firewall to protect their web applications from HTTPbased attacks The course includes. Contents 1 Getting Started;.
Contact Support North America Outside North America Local Support Numbers.

Big Ip Cloud Edition Solution Guide

Installing F5 Big Ip Adc For Anthos Clusters On Vmware Using Manual Load Balancing

Vmware Horizon View Big Ip V11 12 13 Ltm Apm Afm F5
F5 Waf Configuration Guide のギャラリー

Setting Up And Configuring F5 Asm Waf With Dvwa Youtube

F5 Bigip Name Based Reverse Proxy Ltm Policies Somoit Net
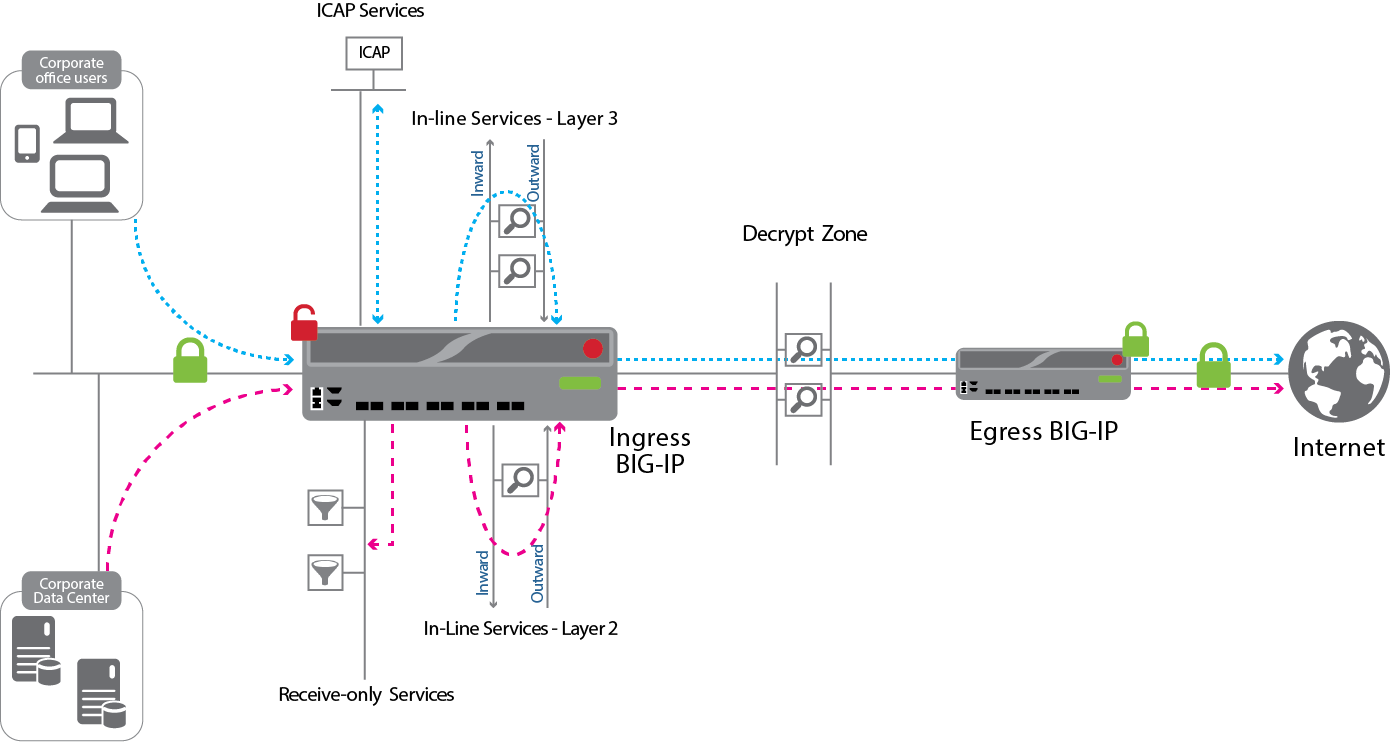
Ssl Intercept V1 5 Big Ip V12 0 Ltm F5

F5 Networks Configuring Big Ip Advanced Waf Web Application Firewall Tlg Learning 800 460 2298

Big Ip Virtual Edition And Microsoft Azure Semi Automatic Web Application Firewall Solution For Azure Security Center Version Pdf Free Download

David Romero Trejo F5 Asm Cookie And Http Header Tampering

Kaazing Com Kaazing Websocket Gateway 5 Docs
Azure And F5 Waf In The Cloud Devcentral

How To Migrate Your F5 Big Ip Exchange Service To Kemp Using Edge Security Pack Load Balancers

F5 Asm Operations Guide Pdf Big Ip Asm Operations Guide A Web Application Firewall That Guards Your Critical Apps With F5 U00a9 Big Ip Aplplication Course Hero

F5 Awaf Vs Asm What S The Difference Between F5 S Asm And Awaf Worldtech It

Complete Web Application Firewall Guide By Rezaduty Devconnected Devops Sysadmins Engineering Medium

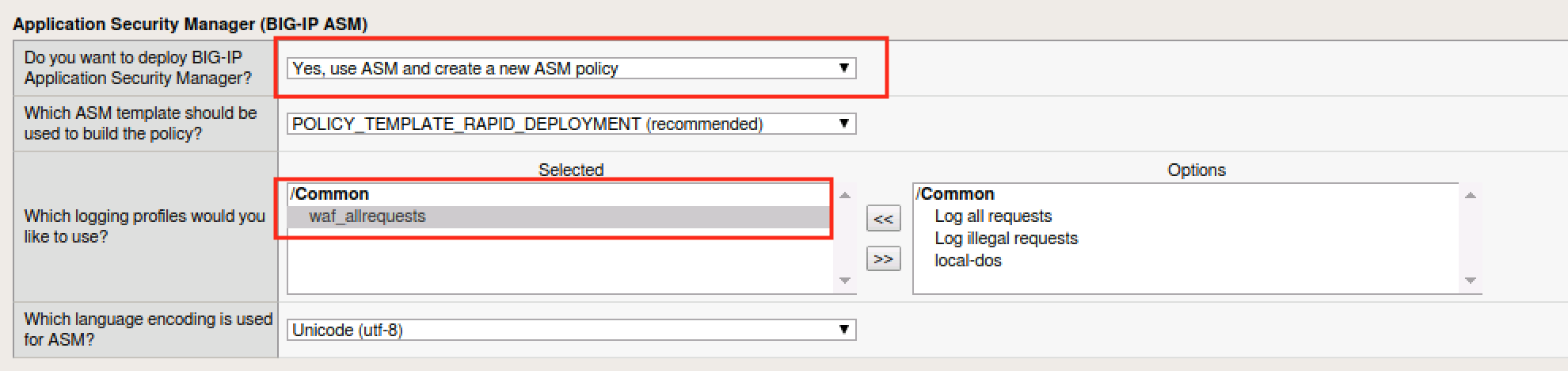
Module 1 Base Policy Creation

Data Center Firewall Big Ip V11 Ltm
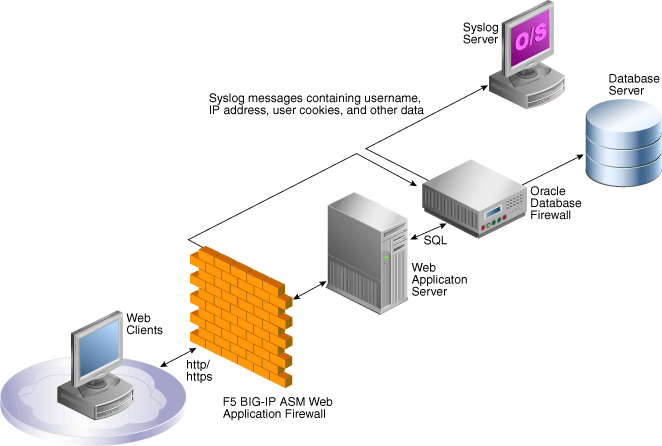
Using Oracle Database Firewall With Big Ip Asm

F5 Apm Configuration Demo Youtube

F5 Bigip Asm Introduction

How To Hack A Company By Circumventing Its Waf For Fun And Profit Part 2 Red Timmy Security

Module 1 Base Policy Creation

F5 Asm Operations Guide Pdf Big Ip Asm Operations Guide A Web Application Firewall That Guards Your Critical Apps With F5 U00a9 Big Ip Aplplication Course Hero

Deploy F5 Across Two Azure Stack Hub Instances Azure Stack Hub Microsoft Docs

Setting Up Ssl Offloading Termination On An F5 Big Ip Load Balancer Lullabot

Aws Marketplace F5 Waf Solution 1gbps
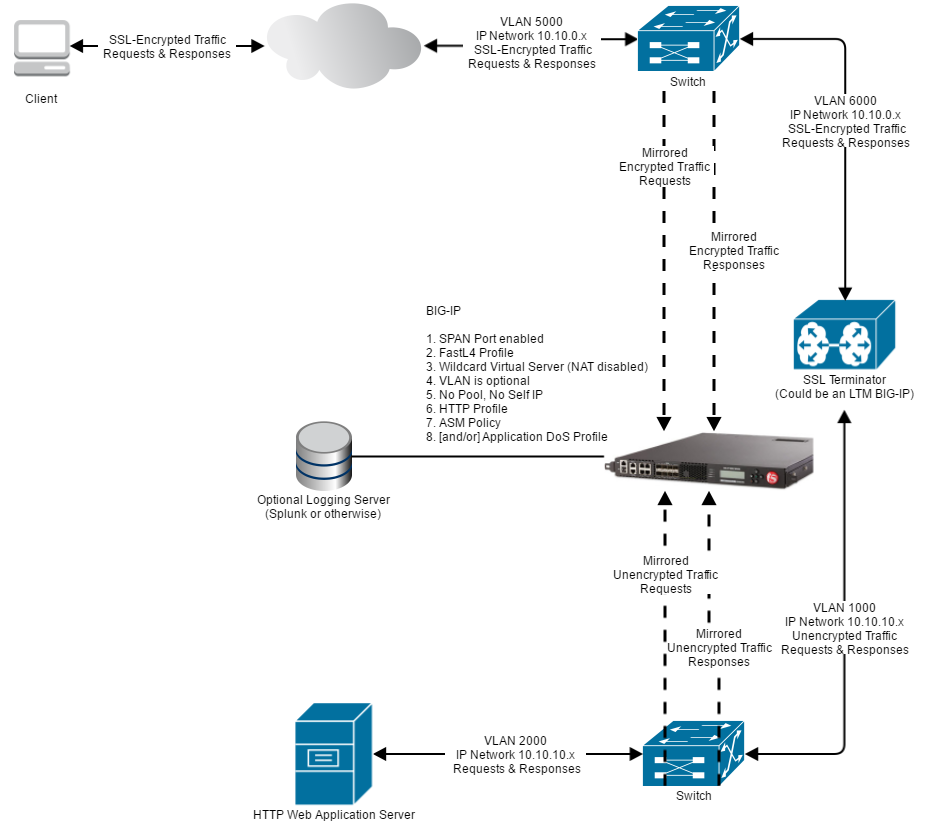
Askf5 Manual Chapter Working With Passive Monitoring

Module 1 Base Policy Creation
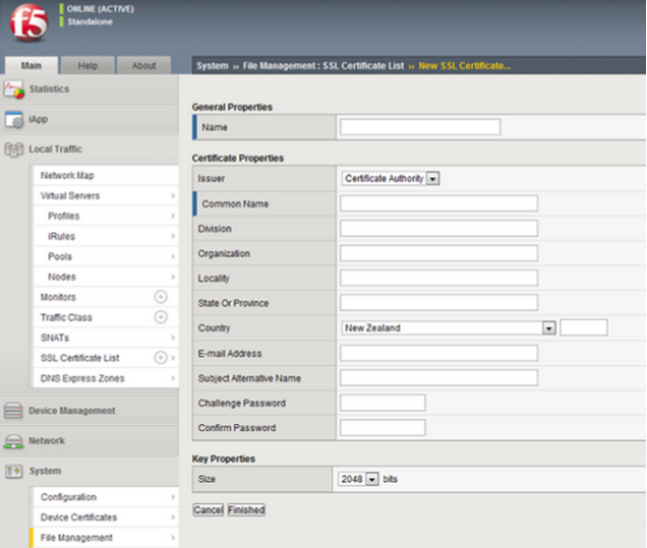
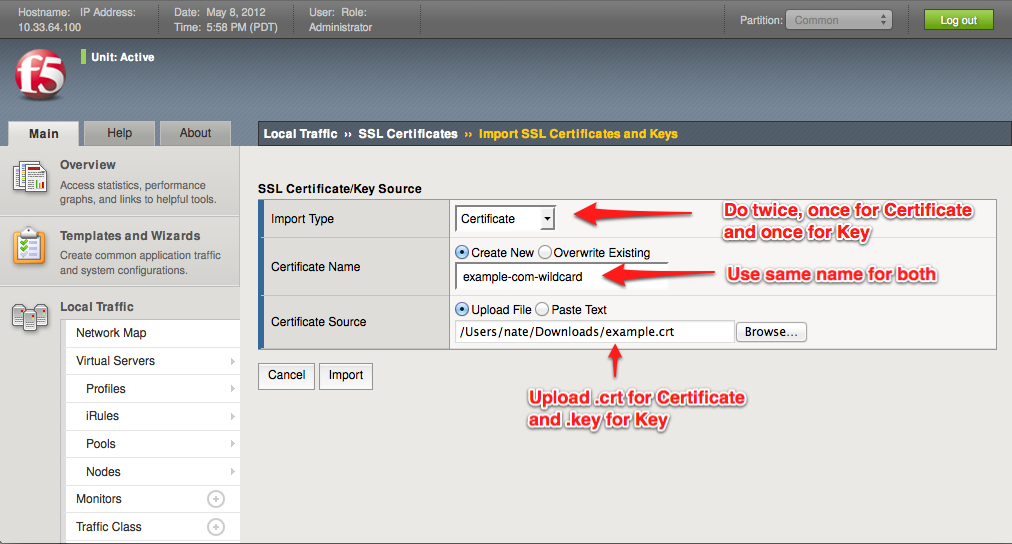
Csr Instructions For F5 Big Ip 11 X

Big Ip Configuration Series Big Ip Web Gui Navigation Youtube
1
Q Tbn And9gcq5uyxnplahgn U0o7 Vtfsfxt Cjqf8kajh1wlfanmrevnysu Usqp Cau
Exercise 1 1 Policy Creation
Just One Post Enabling Declarative Dns With F5 And The Nginx Javascript Module Nginx

2 2 1 Lab 2 Deploy An F5 Web Application Firewall Using The Azure Security Center Azure F5 Lab Days Documentation
Www Veracomp Ro Wp Content Uploads 01 F5 Emea Product Guide Jan Public Pdf
Secure Your New Aws Application With An F5 Web Application Firewall Part 2 Of 4 Devcentral

Installing F5 Big Ip Adc For Anthos Clusters On Vmware Using Manual Load Balancing
F5 Big Ip Asm Waf Rules Report Acunetix

Networking In The Windows World
Exercise 4 0 Iapp With Policy
Azure And F5 Waf In The Cloud Devcentral
Pages Awscloud Com Rs 112 Tzm 766 Images F5 Advanced Waf Getting Started Guide Pdf

Article K Big Ip Asm Operations Guide Chapter 1 Guide Introduction And Contents

F5 Networks Tmos Administration Study Guide By F5 Books Issuu

Exchange 10 With F5 Big Ip And Dell Dell Us
Setting Up Ssl Offloading Termination On An F5 Big Ip Load Balancer Lullabot
Integrating The F5 Bigip With Azure Sentinel Devcentral

Ibm Guardium Big Ip V11 3 Hf 1 Asm
Marketplace Res Cbc Cn Obs Myhwclouds Com App Attachment 1906 78d524ef 9076 4730 Be6e Fbab6c3c3af2 Pdf
Waf Web Application Firewall Guide Ip With Ease

Barracuda Web Application Firewall Vs F5 Big Ip Comparison It Central Station

Configuration Guide For Big Ip Application Security Manager Http Cookie Hypertext Transfer Protocol
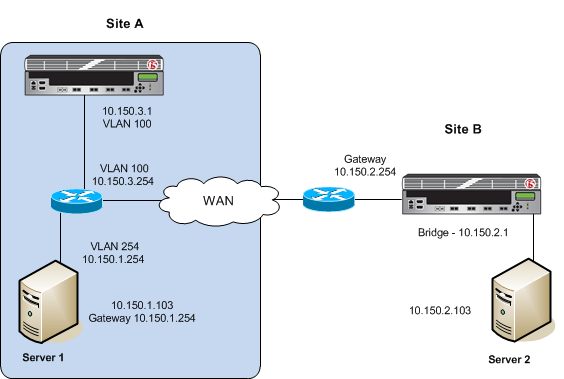
Askf5 Manual Chapter Wccp

Module 1 Base Policy Creation

Configure Irules On F5 Ltm For Ise Radius And Http Loadbalancing Cisco

Microsoft Psilva S Prophecies

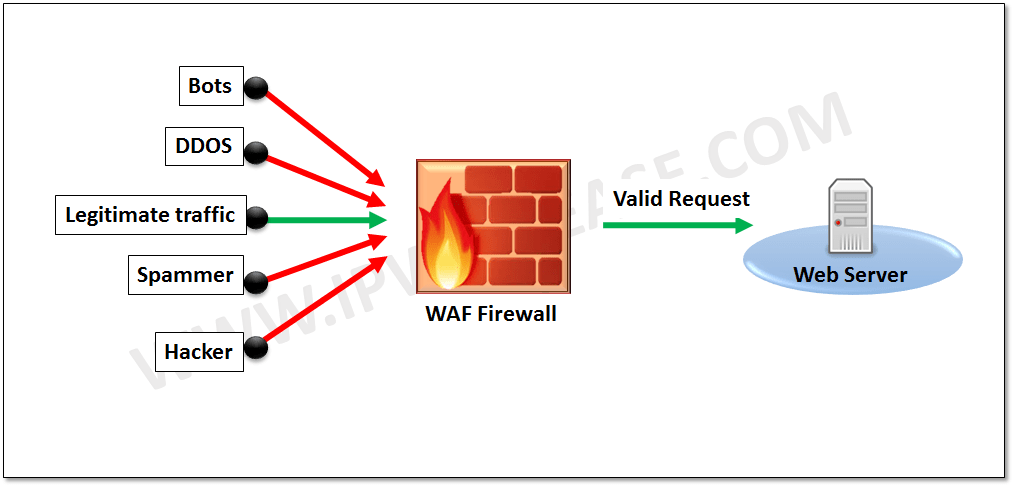
Article K What Is A Waf

2 2 1 Lab 2 Deploy An F5 Web Application Firewall Using The Azure Security Center Azure F5 Lab Days Documentation
Www F5 Com Pdf Products Big Ip Application Security Manager Ds Pdf

Complete Web Application Firewall Guide By Rezaduty Devconnected Devops Sysadmins Engineering Medium
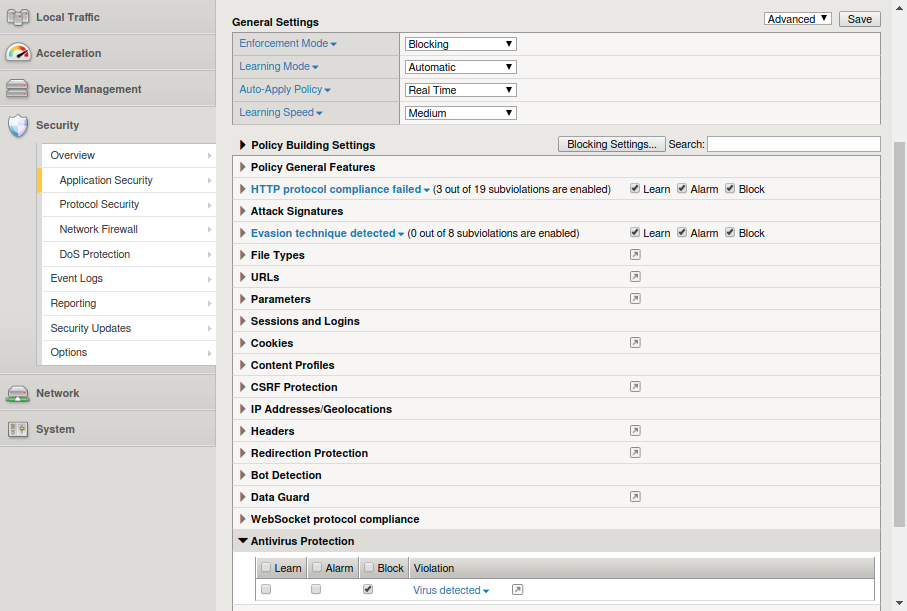
F5 Big Ip Asm Waf Metadefender Icap Server

Module 1 Base Policy Creation
Pages Awscloud Com Rs 112 Tzm 766 Images F5 Advanced Waf Getting Started Guide Pdf

Installing F5 Big Ip Adc For Anthos Clusters On Vmware Using Manual Load Balancing
Www F5 Com Pdf Products Big Ip Application Security Manager Ds Pdf
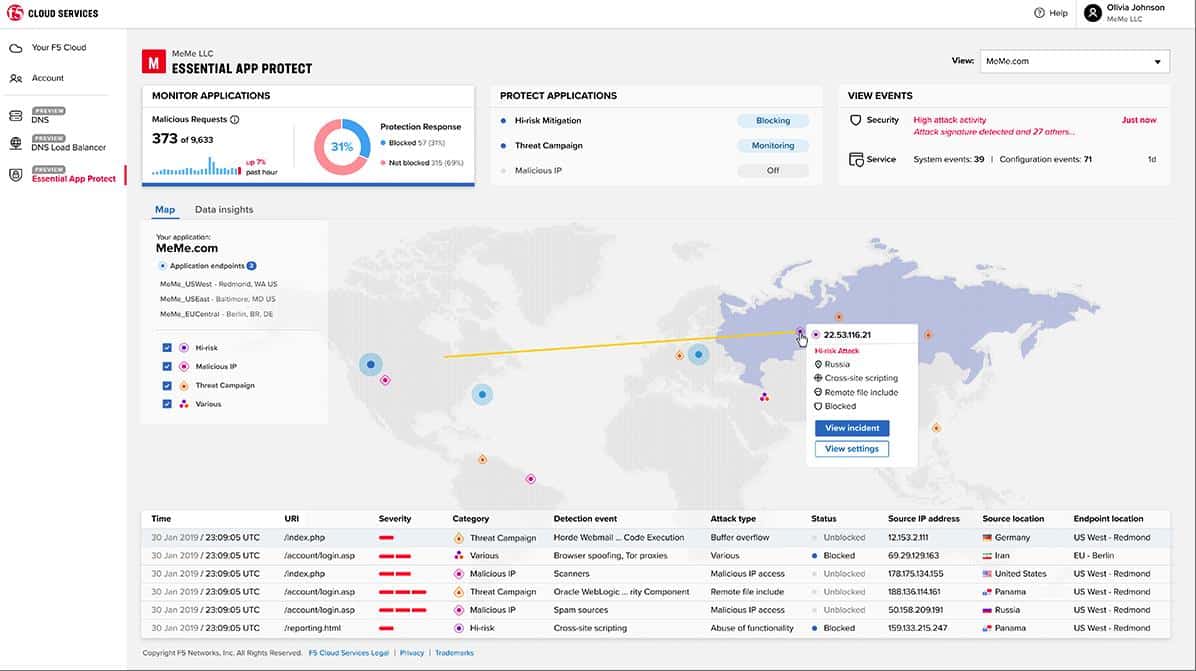
11 Best Web Application Firewalls Waf Buyer S Guide For 21

F5 Big Ip Ve On Aws Quick Start
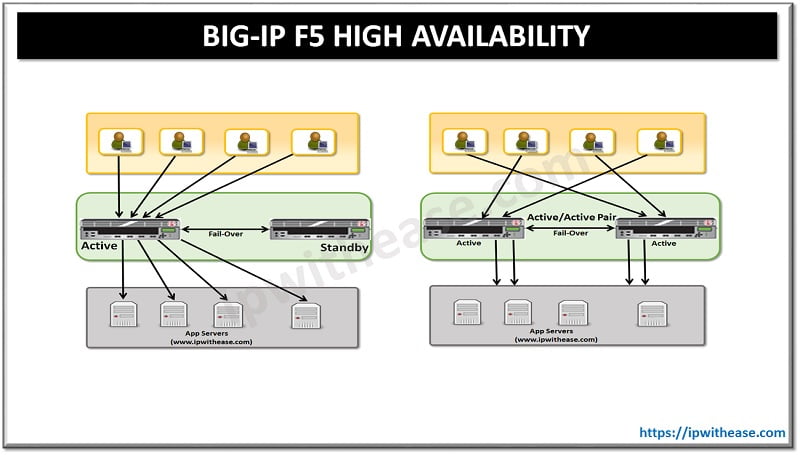
Big Ip F5 High Availability Guide Ip With Ease
Deploying The Big Ip Asm With Oracle Database Firewall Deployment Guide What S Inside Manualzz

Gslb Integration With F5 Gtm

Step By Step Ssl Installation Guide For F5 Big Ip Server

Module 1 Base Policy Creation

F5 Big Ip Gtm With Apm For Global Remote Access Big Ip 11 2 Gtm Apm

F5 Asm Web Application Firewall Youtube

Module 1 Base Policy Creation

Complete Web Application Firewall Guide By Rezaduty Devconnected Devops Sysadmins Engineering Medium

Module 1 Base Policy Creation
F5 Big Ip Asm Waf Rules Report Acunetix
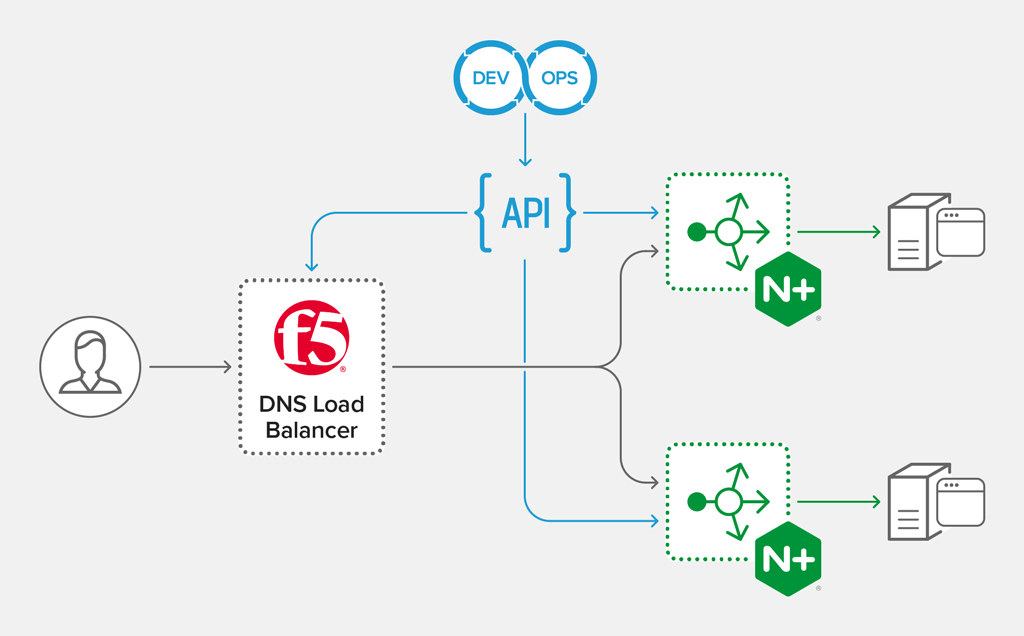
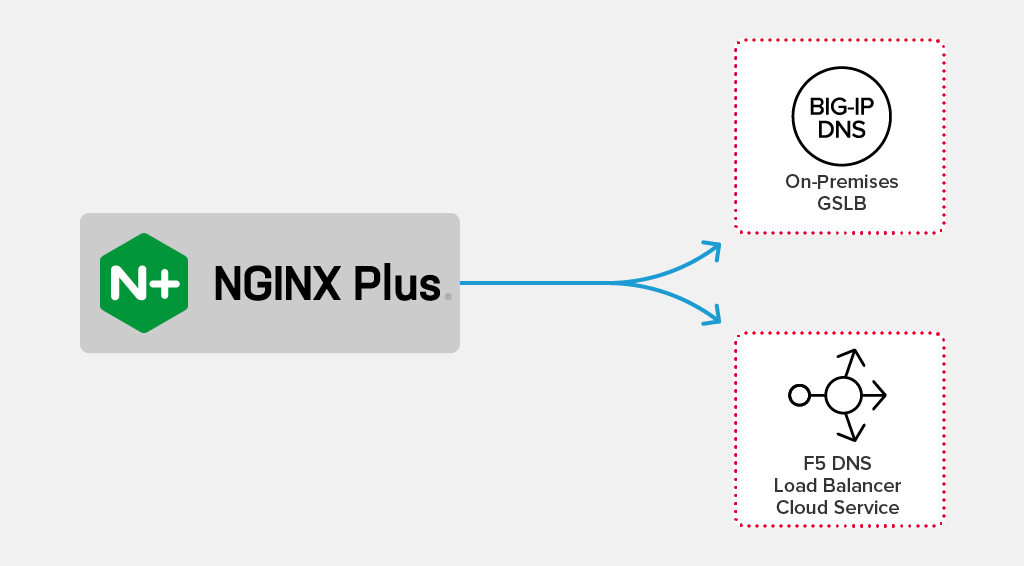
Ensuring Application Availability With F5 Dns Load Balancer Cloud Service And Nginx Plus Nginx

Deploying The Big Ip V11 With Oracle Peoplesoft F5 Networks

Module 1 Base Policy Creation

F5 Web Application Security
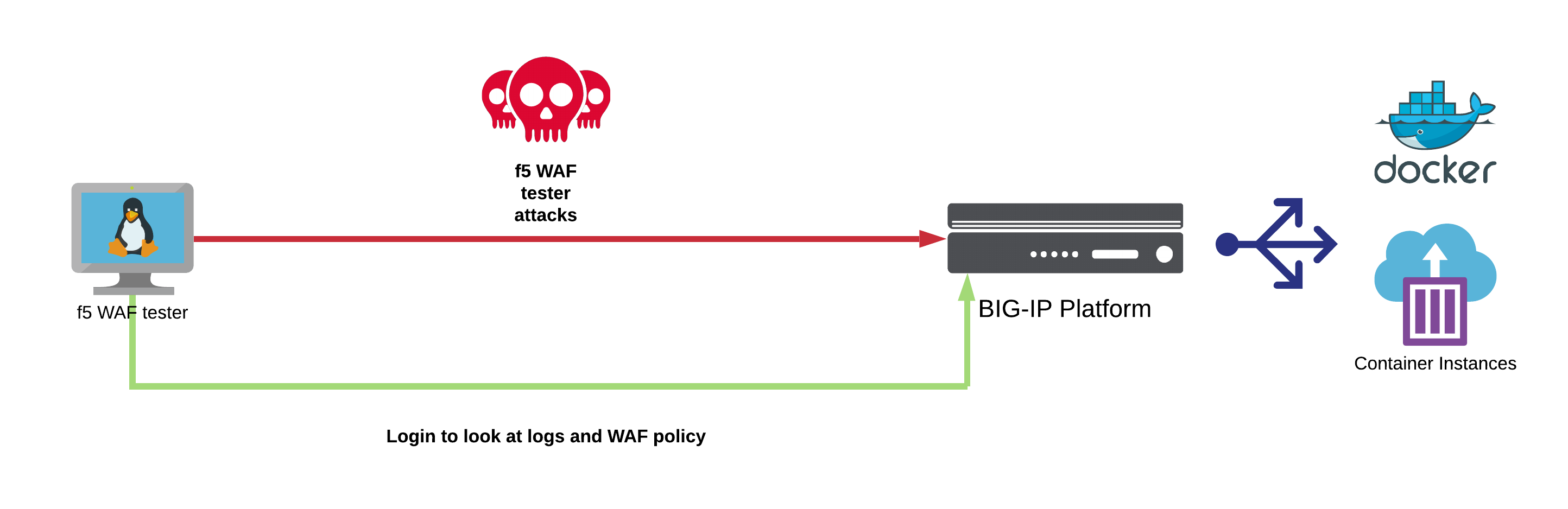
Module 2 Policy Testing Intro To F5 Waf Tester Secops Engineer
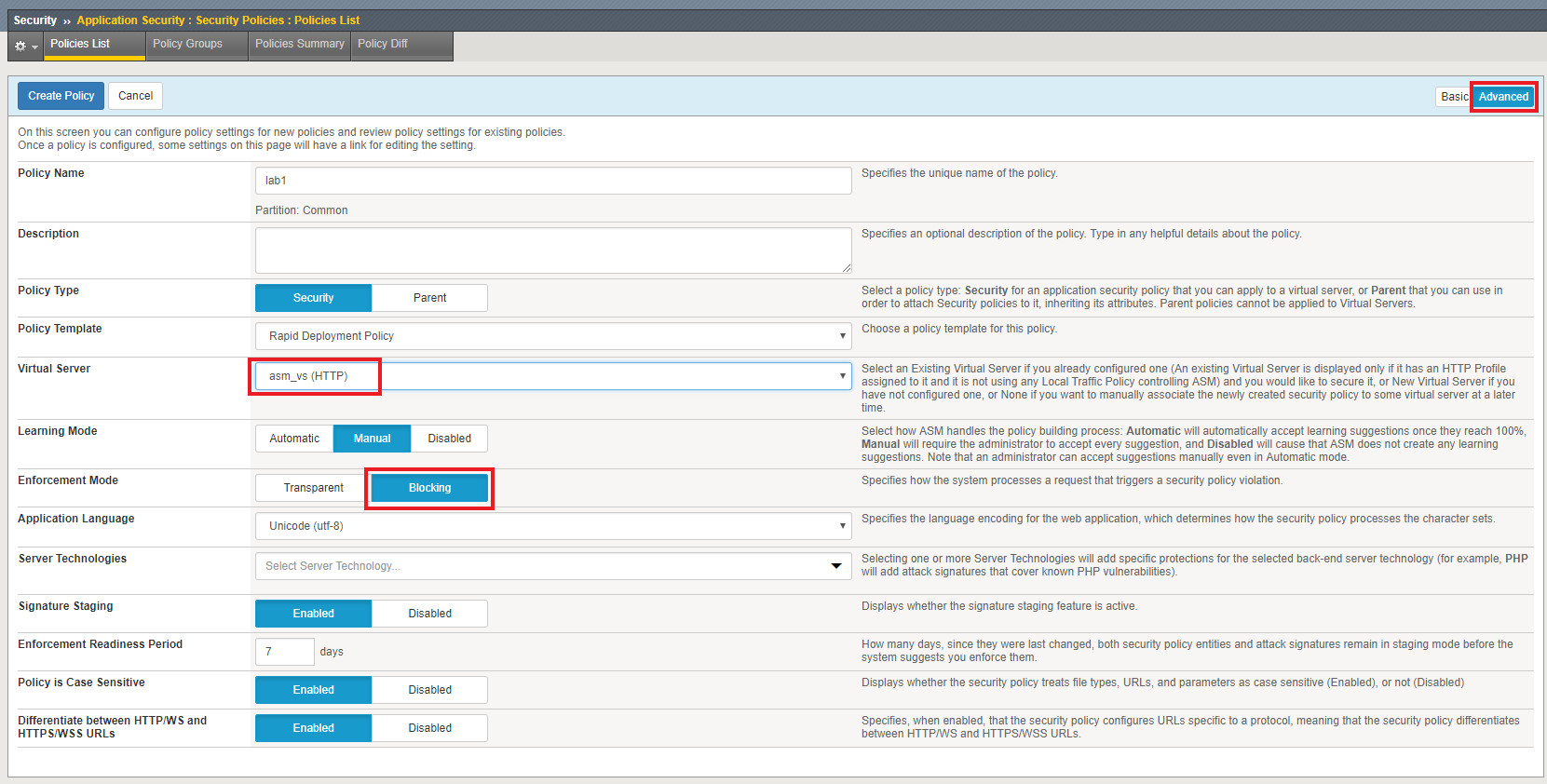
Lab 1 1 Allowed Url List
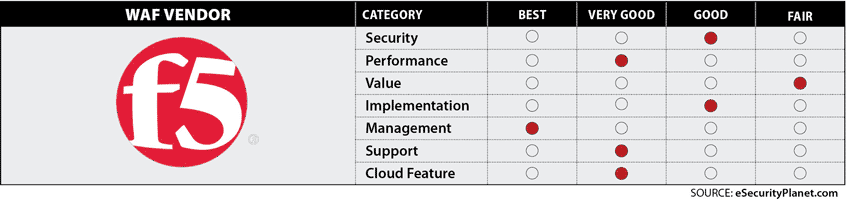
F5 Advanced Waf Esecurity Planet
Media Readthedocs Org Pdf F5 Agility Labs Waf Latest F5 Agility Labs Waf Pdf

Module 1 Base Policy Creation
Q Tbn And9gcqpcbfwhk3oj 4xiqmytxuq8l Ffjrsdayjvhnuif4m Mpe0ljw Usqp Cau

F5 Networks Wikipedia
Www Carahsoft Com Download File View

2 2 1 Lab 2 Deploy An F5 Web Application Firewall Using The Azure Security Center Azure F5 Lab Days Documentation

Azure Marketplace F5 Waf Solution Build5nines

F5 Ddos Protection Recommended Practices Volume 2 Manualzz

In 5 Minutes Big Ip Asm Application Ready Security Templates Youtube
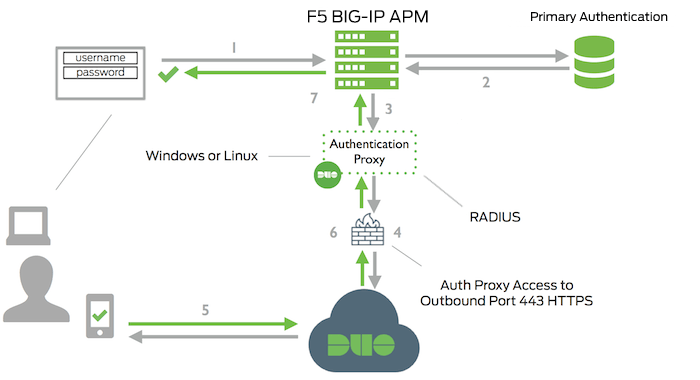
Two Factor Authentication For F5 Big Ip Apm With Radius And Duo Prompt Duo Security
Web Application Firewall 101 Learn All About Wafs

Module 1 Base Policy Creation

Module 1 Base Policy Creation
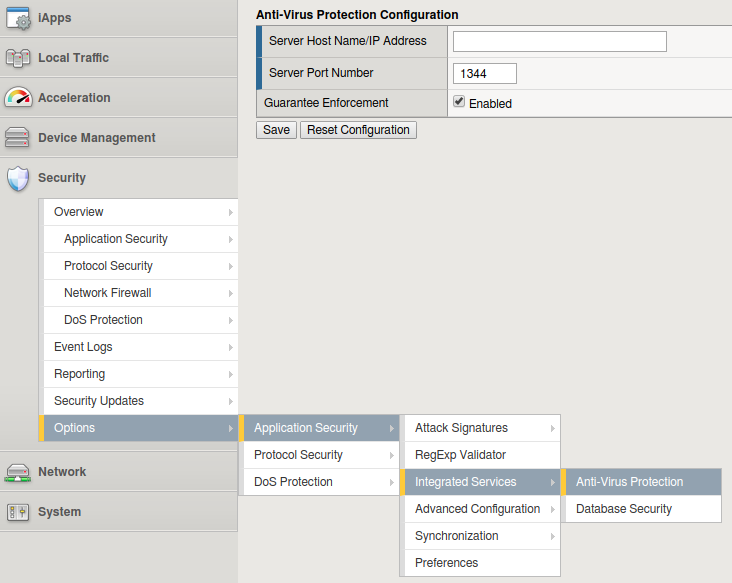
F5 Big Ip Asm Waf Metadefender Icap Server
Pages Awscloud Com Rs 112 Tzm 766 Images F5 Advanced Waf Getting Started Guide Pdf
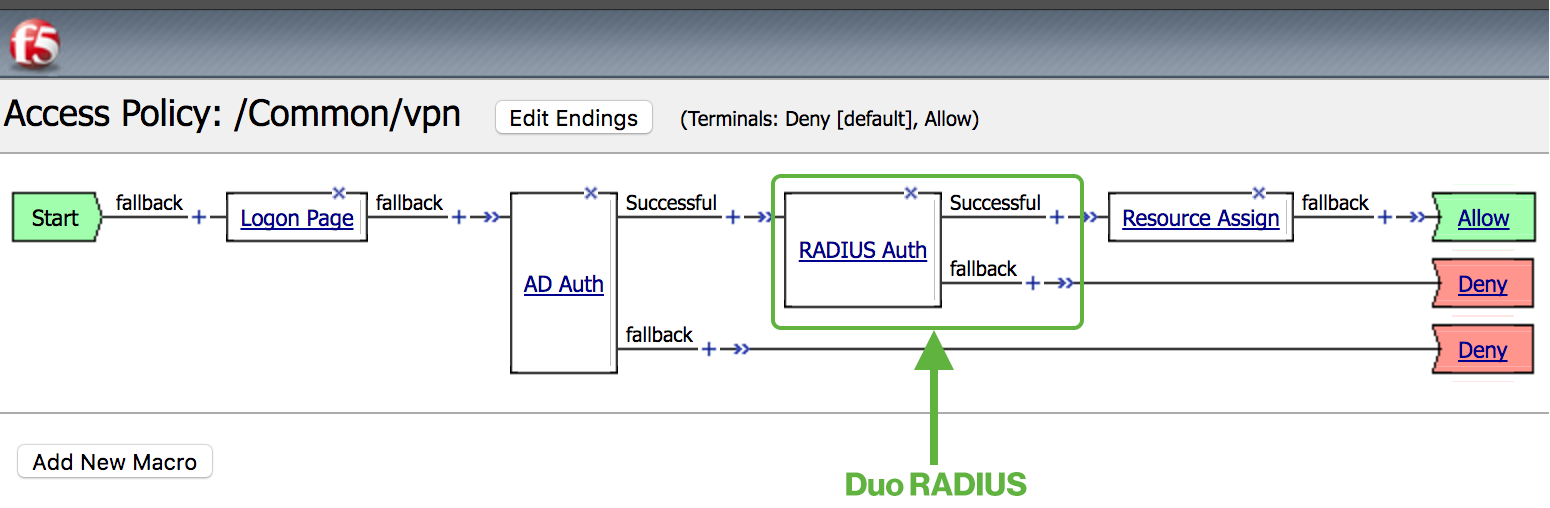
Two Factor Authentication For F5 Big Ip Apm With Radius And Duo Prompt Duo Security

Deploy F5 Across Two Azure Stack Hub Instances Azure Stack Hub Microsoft Docs
Q Tbn And9gcruvafcyzey7iwkgxyz Fmd Gzorxfm0ogd2wpf2q Xpk7ijw1t Usqp Cau



