F5 Waf Architecture
6 F5 WAF in AWS;.
F5 waf architecture. 7 Welcome to F5 Agility 18 – Secure BIGIP and Application deployments in AWS documentation!. Brad Causey discusses the best Web application firewalls in the industry, covering the key points related to selecting WAF products that fit your technical and budgetary needs. By implementing F5 Advanced WAF between applications and end users, businesses can decrypt and inspect all traffic before it enters the network or reaches the server in the cloud The WAF will then use advanced detection and mitigation techniques to prevent customer data from being accessed, manipulated, or stolen.
Reference Architecture › Silverline WAF Trial 24x7 access to the experts in the F5 Security Operations Center (SOC) Prior to starting the trial, we’ll work with you to put together a success criteria document, so we both understand what a successful trial looks like. While they are mostly known for topoftheline networking devices, F5 Networks may not provide security space in the device afterthought Accessible as a standalone appliance or module for one of its network goods, the BIGIP Application Protection Manager (ASM) acts as an application firewall, securing web apps and utilities with a strong policy driver. 63 Explore the F5 BigIP Virtual Editions Deployed;.
63 Explore the F5 BigIP Virtual Editions Deployed;. The F5 BIGIP platform provides various services to help you enhance the security, availability, and performance of your apps These services include, L7 load balancing, network firewalling, web. 6 F5 WAF in AWS 61 Infrastructure As Code;.
An AWS application load balancer terminating TLS is a prerequisite for deploying WAF rules From the AWS Console, navigate to Services => Security, Identity & Compliance => WAF & Shield Click the Go to AWS WAF button Prior to deploying F5 WAF Rules for AWS, you need to subscribe to the service and agree to the AWS subscription agreement. The BIGIP Virtual Edition (VE) is the industry’s most trusted and comprehensive app delivery and security solution Providing everything from intelligent traffic management and visibility, to app security, access, and optimization, BIGIP VE ensures your apps are fast, available, and secure wherever they are deployed. F5 BIGIP is most compared with Citrix ADC, HAProxy, A10 Networks Thunder ADC, Fortinet FortiWeb and NGINX Plus, whereas Microsoft Azure Application Gateway is most compared with AWS WAF, HAProxy, F5 Advanced WAF, Cloudflare and Fortinet FortiWeb See our F5 BIGIP vs Microsoft Azure Application Gateway report.
Contact Support North America or Outside North America Local Support Numbers. F5 Rules for AWS WAF Web exploits OWASP Rules Sold by F5 Networks Protect against web exploits F5 Web Exploits Rules for AWS WAF, provides protection against web attacks that are part of the OWASP Top 10, such as SQLi, XSS, command injection, NoSQLi injection, path traversal, and predictable resource. The BIGIP Virtual Edition (VE) is the industry’s most trusted and comprehensive app delivery and security solution Providing everything from intelligent traffic management and visibility, to app security, access, and optimization, BIGIP VE ensures your apps are fast, available, and secure wherever they are deployed.
Advanced Web Application Firewall (WAF) Protect your apps with behavioral analytics, proactive bot defense, and applicationlayer encryption of sensitive data Use the ROI Estimator from F5 and Forrester to find out how Advanced WAF can improve your security posture and save you money Estimate the ROI of Advanced WAF. The first idea that came to mind was to use a web application firewall (WAF) It makes sense, right?. The F5 SSL Everywhere reference architecture is centered on the custombuilt SSL software stack that is part of every F5 BIGIP Local Traffic Manager (LTM) deployment This white paper identifies many of the customer scenarios where visibility, programmability, and management come together to form complete ecosystems for securing data in transit.
Web application firewall software is generally available as a web server plugin or an inline web server Whether software or hardware, a web application firewall analyzes the GET and POST requests sent through HTTP and HTTPS, and applies configured firewall rules to identify and filter out malicious web traffic. The course includes lecture, handson labs, and discussion about different F5 Advanced Web Application Firewall tools for detecting and mitigating threats from multiple attack vectors such web scraping, Layer 7 Denial of Service, brute force, bots, code injection, and zero day exploits. 3 Class PC 101 Deploying F5 Solutions to AWS with CloudFormation Templates;.
Firewalls have, for the longest time, been considered a critical line of defense against attacks from outside of an organization If you’re not familiar with the term, a WAF is a specialpurpose firewall for HTTP/Sbased applications Quoting. 4 PC211 Secure Azure Computing Architecture;. Figure 2 AWS WAF Security Automations architecture on AWS At the core of the design is an AWS WAF web ACL, which acts as the central inspection and decision point for all incoming requests to a web application During initial configuration of the AWS CloudFormation stack, the user defines which protective components to activate.
The WAF will then use advanced detection and mitigation techniques to prevent customer data from being accessed, manipulated, or stolen F5 Advanced WAF provides advanced layer 7 (L7) security, protecting against L7 Denial of Service (DoS) attacks, malicious bot traffic, Open Web application Security Project (OWASP) Top 10 threats, and much more. HTTPS to the WAF ELB URL Refresh the browser with for 15 seconds to generate a modest amount of traffic Back in the CloudWatch console Use the search term waf to see logs coming from your F5 WAF. Web Application Firewall allows you to configure request size limits within lower and upper bounds The following two size limits configurations are available The maximum request body size field is specified in kilobytes and controls overall request size limit excluding any file uploads This field has a minimum value of 1 KB and a maximum.
5 Public Cloud Architectures II F5 in AWS Advanced Use Cases Beyond Native Tools;. F5's auto scaling WAF solution employs BIGIP ASM and BIGIP LTM to provide advanced firewall protection, securing your applications against layer 7 DDoS attacks, malicious bot traffic and other common application vulnerabilities while offering powerful reporting and automated learning capabilities. F5 Positioned as a Leader in 17 Gartner Magic Quadrant for Web Application Firewalls Get Gartner’s independent analysis to evaluate Web Application Firewall (WAF) solutions for your organisation Read the report to learn • WAF market trends.
Contact Support North America or Outside North America Local Support Numbers. 3 Class PC 101 Deploying F5 Solutions to AWS with CloudFormation Templates;. 6 F5 WAF in AWS 61 Infrastructure As Code;.
BIGIP Local Traffic Manager Delivers intelligent traffic management, as well as SSL offload and application optimization, for the best enduser experience F5 Advanced Web Application Firewall Provides an advanced WAF solution to protect all your applications against automated web attacks,. F5 BIGIP WAF Declarative Policy WAF specific configurations on a BIGIP system by using a declarative policy model. F5 BIGIP DNS (GTM) V13;.
3 Class PC 101 Deploying F5 Solutions to AWS with CloudFormation Templates;. This is F5’s Web Application Firewall (WAF), if you understand how traditional firewalls block and allow traffic by means of IP & Ports, you can think of the F5 ASM as filtering and protecting everything after the slash “/” in your URL – specifically on the contents of requests to your web application, including the URIs and posted parameters. F5 Application WAF is a one package solution for public ,private and onpremises deployment over cloud It provides many cool functionalities like security services, site wide behavioral analysis, 3rd party DAST Tools.
F5 Rules for AWS WAF Bot Protection Rules Sold by F5 Networks Protect against automated attacks Bot Protections Rules is a partner managed rule group for AWS WAF that stops a broad range of malicious bots activities such as vulnerability scanners, web scrapers, DDoS tools, and forum spam tools. Service Discovery iApp for dynamically populating pool members using instance tags. AWS WAF is most compared with Microsoft Azure Application Gateway, Akamai Kona Site Defender, Imperva Web Application Firewall, Cloudflare and Fortinet FortiWeb, whereas F5 BIGIP is most compared with Citrix ADC, HAProxy, A10 Networks Thunder ADC, Fortinet FortiWeb and Imperva Web Application Firewall See our AWS WAF vs F5 BIGIP report.
Recently, I had the opportunity to participate in a podcast with the team at F5 Christine Puccio – VP of Global Cloud Alliances and Heath Parrott – Senior Global Solutions Architect for Cloud discussed their latest announcement the integration between F5 Essential App Protect, a web application firewall (WAF) SaaS solution and Amazon CloudFront, a content delivery network (CDN) solution. 1 One Arm Deployment 2 Two Arm Deployment 3 Direct Server Return DSR. F5 Rules for AWS WAF Bot Protection Rules Sold by F5 Networks Protect against automated attacks Bot Protections Rules is a partner managed rule group for AWS WAF that stops a broad range of malicious bots activities such as vulnerability scanners, web scrapers, DDoS tools, and forum spam tools.
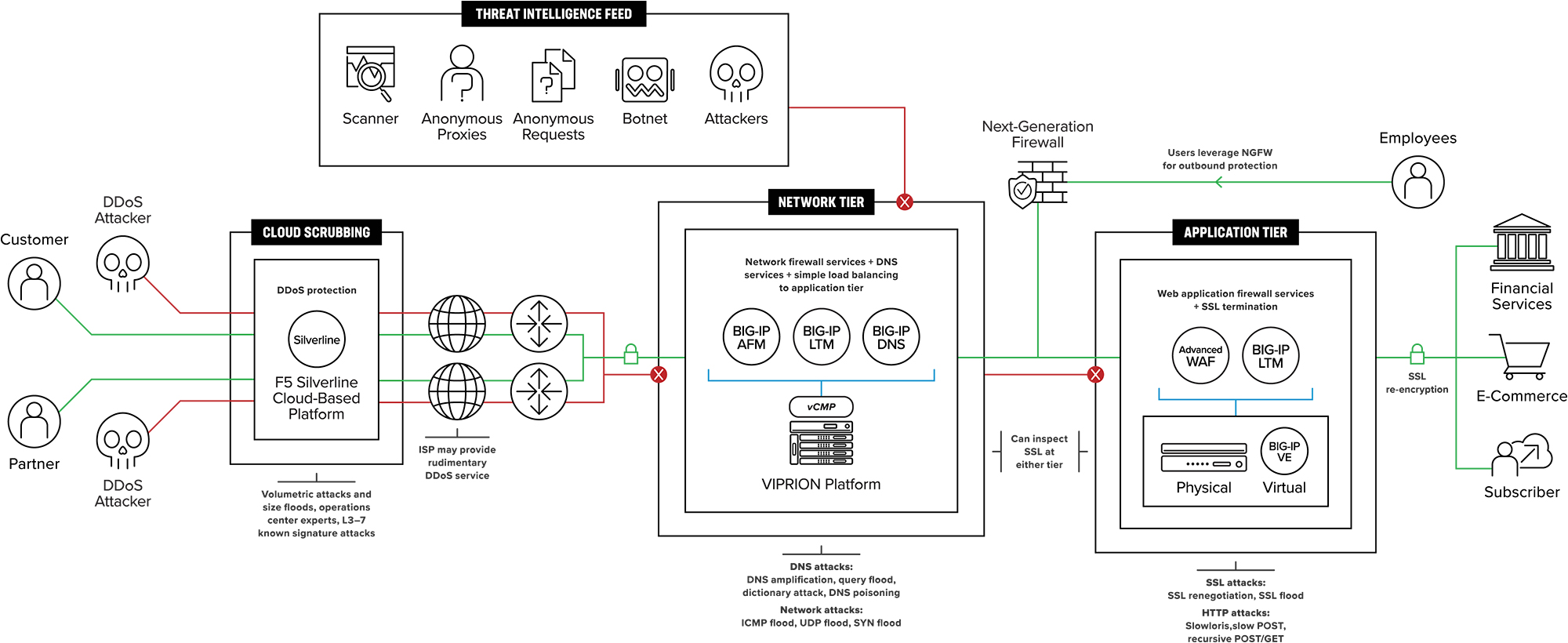
Working with these customers, F5 has developed a DDoS Protection reference architecture that includes both cloud and onpremises components The reference architecture includes multiple tiers of onpremises defenses to protect layers 3 through 7 The network defense tier protects DNS and layers 3 and 4. F5 WAF in AWS¶ This class covers the following topics Deploying AWS environments with CloudFormation Templates and Terraform;. 4 PC211 Secure Azure Computing Architecture;.
F5's auto scaling WAF solution employs BIGIP ASM and BIGIP LTM to provide advanced firewall protection, securing your applications against layer 7 DDoS attacks, malicious bot traffic and other common application vulnerabilities while offering powerful reporting and automated learning capabilities. F5 Advanced WAF is ranked 2nd in Web Application Firewall (WAF) with 13 reviews while F5 BIGIP is ranked 1st in Web Application Firewall (WAF) with 23 reviews F5 Advanced WAF is rated , while F5 BIGIP is rated 80 The top reviewer of F5 Advanced WAF writes "It is very stable as as a load balancer or a web application firewall". By implementing F5 Advanced WAF between applications and end users, businesses can decrypt and inspect all traffic before it enters the network or reaches the server in the cloud The WAF will then use advanced detection and mitigation techniques to prevent customer data from being accessed, manipulated, or stolen.
A web application firewall (WAF) protects web applications from a variety of application layer attacks such as crosssite scripting (XSS), SQL injection, and cookie poisoning, among othersAttacks to apps are the leading cause of breaches—they are the gateway to your valuable data With the right WAF in place, you can block the array of attacks that aim to exfiltrate that data by. F5 believes an inline, full proxy architecture is the most superior deployment model for detecting bad actors, decrypting modern SSL/TLS, monitoring server behavior, and preventing data leakage The superior architecture, performance, and capabilities of F5 Advanced WAF sets it apart in the WAF market Can Advanced WAF run in the Cloud?. F5 WAF in AWS¶ This class covers the following topics Deploying AWS environments with CloudFormation Templates and Terraform;.
Service Discovery iApp for dynamically populating pool members using instance tags. F5 WAF in AWS¶ This class covers the following topics Deploying AWS environments with CloudFormation Templates and Terraform;. F5LTMBasics of Load balancing configuration and concepts Subscribe for more on Automation Duration 5137 Tech NK 49,128 views 5137 BIGIP VE in Microsoft Azure Duration.
F5 Application WAF is a one package solution for public,private and onpremises deployment over cloud It provides many cool functionalities like security services, site wide behavioral analysis, 3rd party DAST Tools. AWS WAF is most compared with Microsoft Azure Application Gateway, Akamai Kona Site Defender, Imperva Web Application Firewall, Cloudflare and Fortinet FortiWeb, whereas F5 BIGIP is most compared with Citrix ADC, HAProxy, A10 Networks Thunder ADC, Fortinet FortiWeb and Imperva Web Application Firewall See our AWS WAF vs F5 BIGIP report. Application Security Manager (ASM) This is F5’s Web Application Firewall (WAF), if you understand how traditional firewalls block and allow traffic by means of IP & Ports, you can think of the F5 ASM as filtering and protecting everything after the slash “/” in your URL – specifically on the contents of requests to your web application, including the URIs and posted parameters.
5 Public Cloud Architectures II F5 in AWS Advanced Use Cases Beyond Native Tools;. AWS Solution Architect (Associate). F5 Application WAF is a one package solution for public,private and onpremises deployment over cloud It provides many cool functionalities like security services, site wide behavioral analysis, 3rd party DAST Tools Also it provides visibility.
With Managed Rules for AWS WAF, you can quickly get started and protect your web application or APIs against common threatsYou can select from many rule types, such as ones that address issues like the Open Web Application Security Project (OWASP) Top 10 security risks, threats specific to Content Management Systems (CMS), or emerging Common Vulnerabilities and Exposures (CVE). With Managed Rules for AWS WAF, you can quickly get started and protect your web application or APIs against common threatsYou can select from many rule types, such as ones that address issues like the Open Web Application Security Project (OWASP) Top 10 security risks, threats specific to Content Management Systems (CMS), or emerging Common Vulnerabilities and Exposures (CVE). 5 Public Cloud Architectures II F5 in AWS Advanced Use Cases Beyond Native Tools;.
The F5 BIGIP platform provides various services to help you enhance the security, availability, and performance of your apps These services include, L7 load balancing, network firewalling, web. The WAF will then use advanced detection and mitigation techniques to prevent customer data from being accessed, manipulated, or stolen F5 Advanced WAF provides advanced layer 7 (L7) security, protecting against L7 Denial of Service (DoS) attacks, malicious bot traffic, Open Web application Security Project (OWASP) Top 10 threats, and much more. This is F5’s Web Application Firewall (WAF), if you understand how traditional firewalls block and allow traffic by means of IP & Ports, you can think of the F5 ASM as filtering and protecting everything after the slash “/” in your URL – specifically on the contents of requests to your web application, including the URIs and posted parameters.
F5 BIGIP ASM (WAF) V13;. Service Discovery iApp for dynamically populating pool members using instance tags. Preconfigured WebACLs are offered by F5, offer protection against common OWASP top 10 style attacks, and can be deployed on any ALB Functionality is a small subset of marketleading F5 WAF running on a BigIP VE Highlight the Listeners tab A listener is ready to receive traffic on HTTPS 443.
Firewall 90 Configuration & Management;. F5 needs to encapsulate the VxLAN packet meant for the pods This requires the sdnservices license addon A VxLAN device needs to be created and the pod overlay network needs to be routed through this device F5 needs to know the VTEP IP address of the pod, which is the IP address of the node where the pod is located. 4 PC211 Secure Azure Computing Architecture;.
Traffic Manager is a DNSbased traffic load balancer that enables you to distribute traffic optimally to services across global Azure regions, while providing high availability and responsiveness Because Traffic Manager is a DNSbased loadbalancing service, it load balances only at the domain level For that reason, it can't fail over as quickly as Front Door, because of common challenges. F5 needs to encapsulate the VxLAN packet meant for the pods This requires the sdnservices license addon A VxLAN device needs to be created and the pod overlay network needs to be routed through this device F5 needs to know the VTEP IP address of the pod, which is the IP address of the node where the pod is located. Watch this video to understand deployment scenarios for F5 Load Balancer!.

Installing F5 Big Ip Adc For Anthos Clusters On Vmware Using Manual Load Balancing
Q Tbn And9gcslrmc Hkisklbxj4ijm6ht Fgk3 Xaw1wufa Nefq86sw4idgl Usqp Cau

Visibility And Management Of Outbound Ssl Traffic Using F5 Solutions Part 2 Veracomp We Inspire It
F5 Waf Architecture のギャラリー

Architecting On Aws Accelerator Tlg Learning 800 460 2298
Q Tbn And9gcrdj2bav13vt7awlq21p9dc1cxjdajqsvwyfugwr0vqjkdfq4sx Usqp Cau
Www Cisco Com C Dam En Us Solutions Collateral Data Center Virtualization Application Centric Infrastructure Solution Overview C22 Pdf
Advanced Aws Waf

How To Enhance Your Application Security Strategy With F5 On Aws Youtube

F5 Big Ip Virtual Edition Ibm Cloud Architecture Center
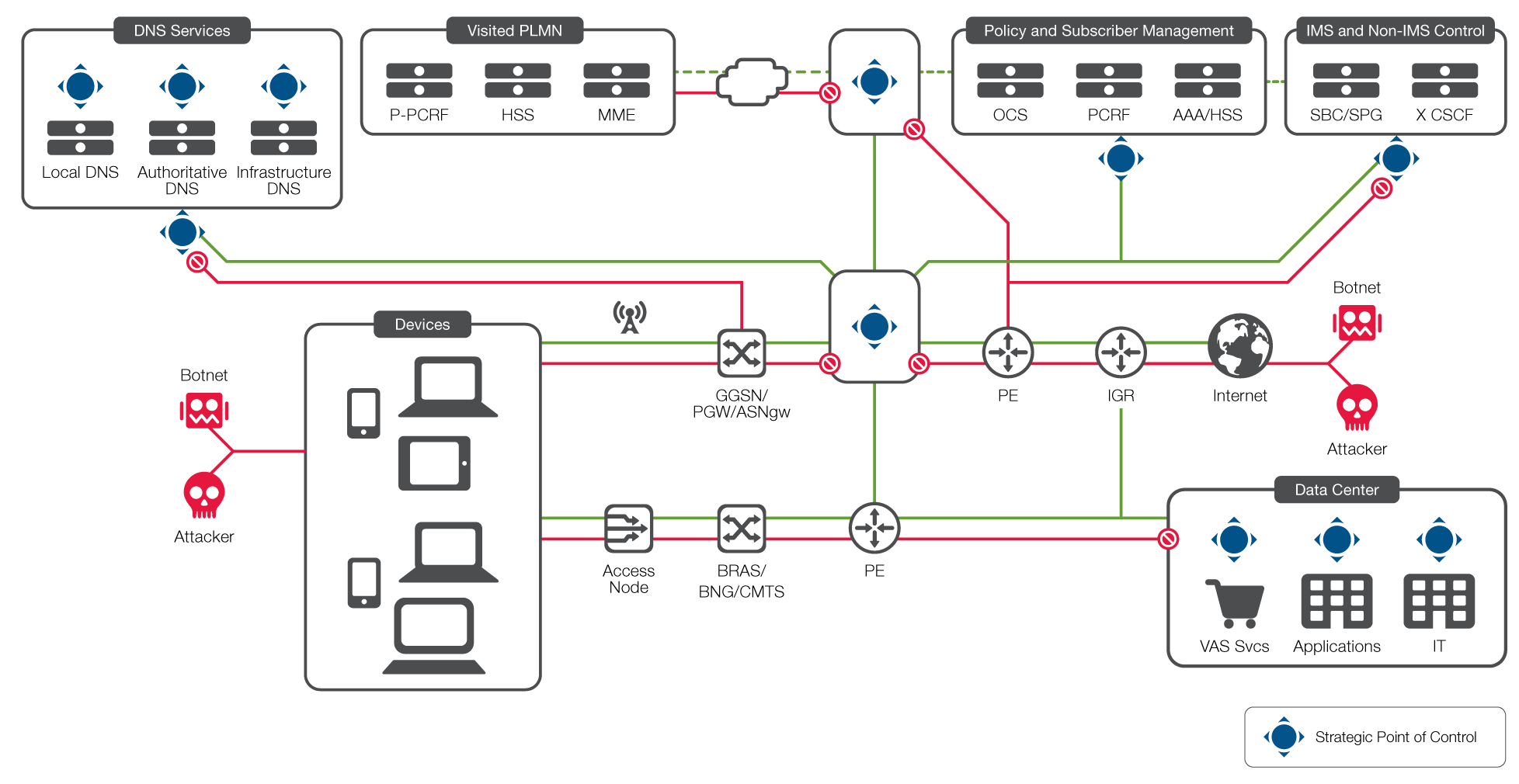
The F5 Security For Service Providers Reference Architecture
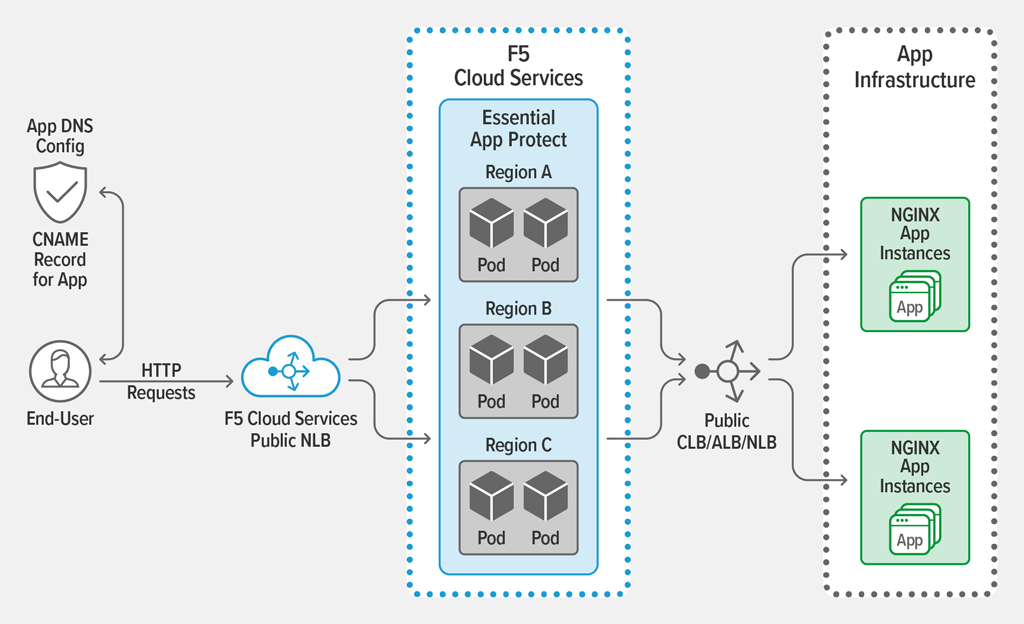
Setting Up App Security As A Service For Nginx In Under 5 Minutes With F5 Essential App Protect Nginx
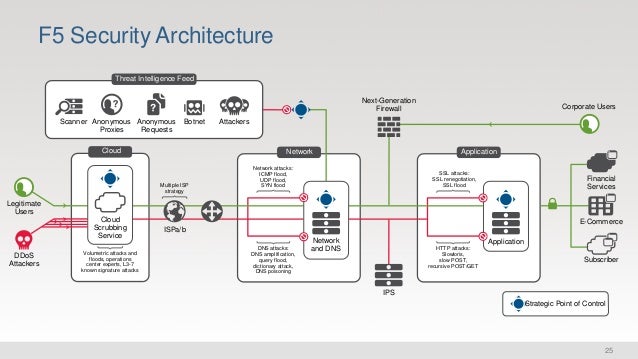
Bezpecnostni Architektura F5
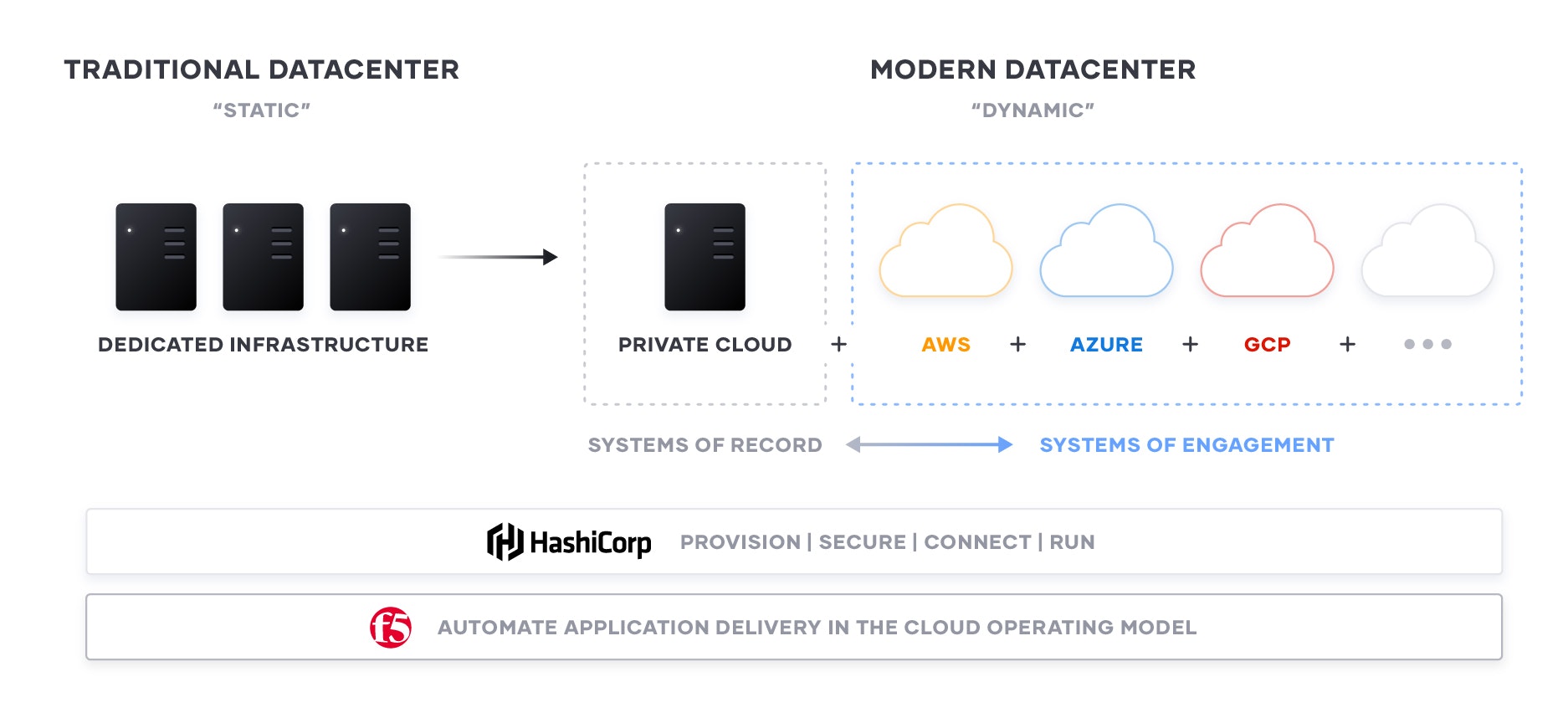
Automating Application Delivery In The Cloud Operating Model With F5

F5 Nginx Ingress Controller And App Protect In A Cloud Native Container World Amazic World

2 2 1 Lab 2 Deploy An F5 Web Application Firewall Using The Azure Security Center Azure F5 Lab Days Documentation

F5 S Unified Architecture Vision
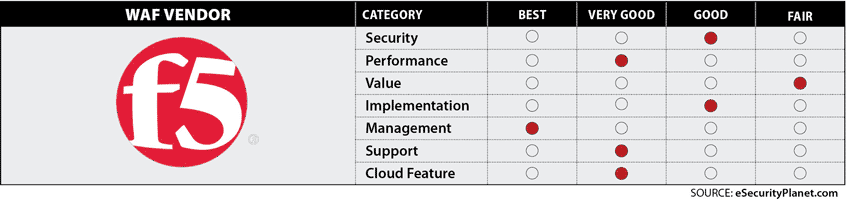
F5 Advanced Waf Esecurity Planet
Silverline Waf Architecture Devcentral
Www Westconcomstor Com Content Dam Wcgcom Us En Westcon Vendors F5 Documentation F5 Solutions Playbook September 16 Pdf
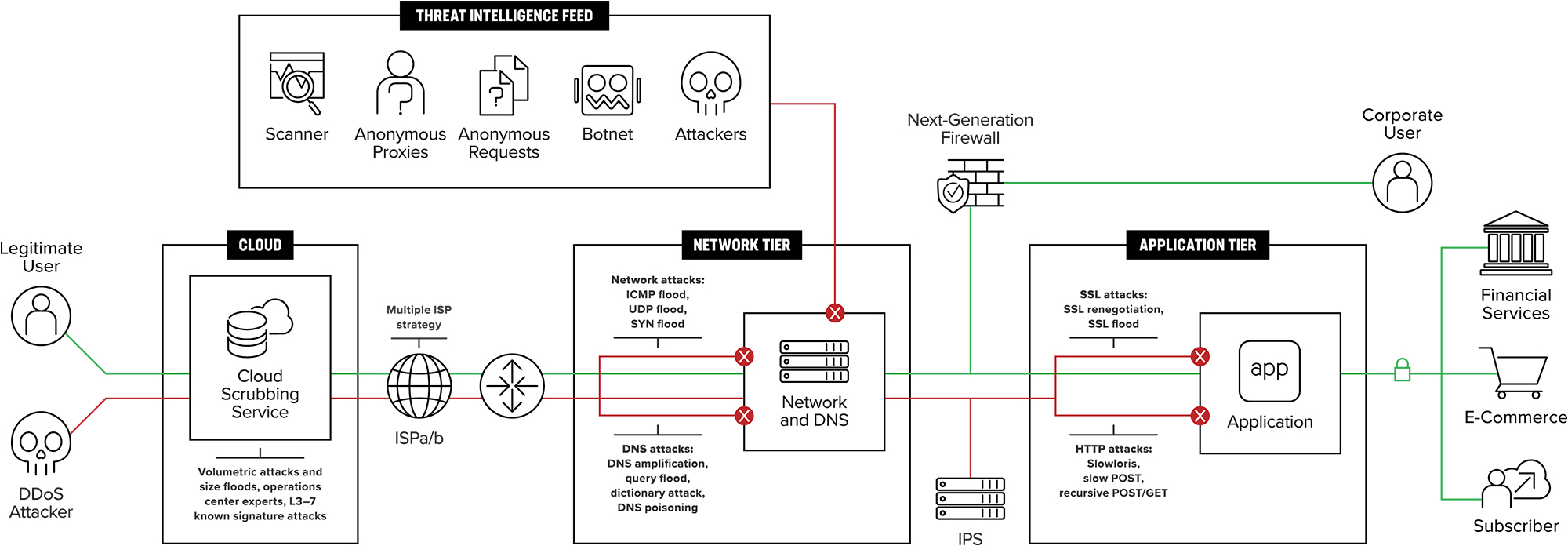
Ddos Architecture Diagrams And White Paper F5

Getting Started With F5 Networks Advanced Waf

Installing F5 Big Ip Adc For Anthos Clusters On Vmware Solutions
Avi Networks Vs F5 Networks Avi Networks
Worldtechit Com Wp Content Uploads 15 07 F5 White Paper The F5 Ddos Protection Reference Architecture Pdf
F5 Big Ip Network Traffic Firewall Load Balancer Code Exploit Cyber Security
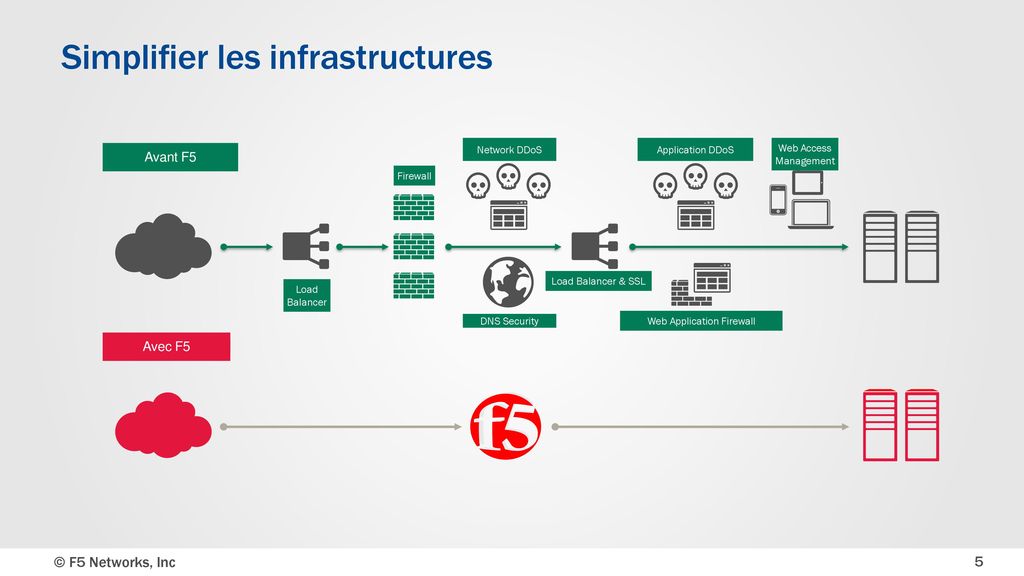
Presentation Offre F5 Amine Fergoug Ppt Download
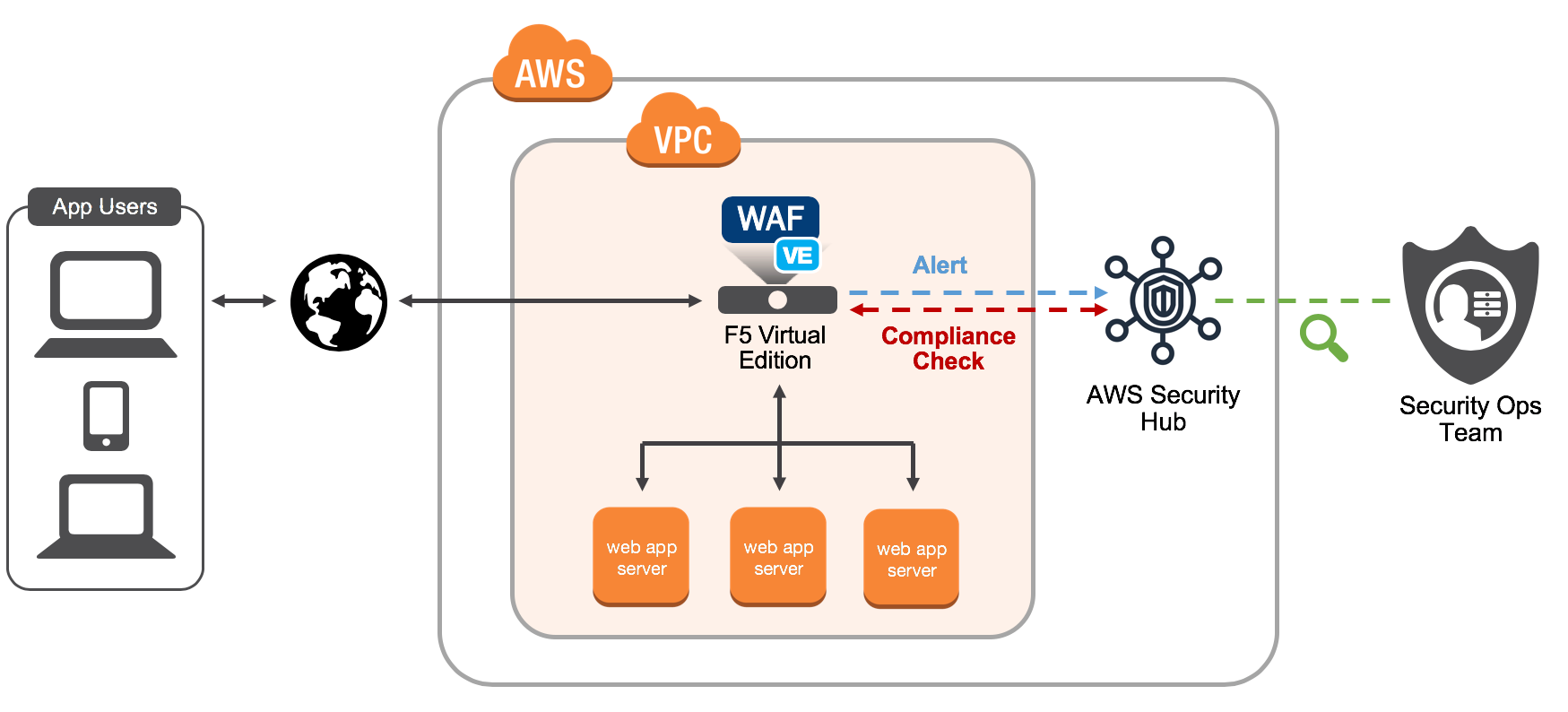
F5 Waf Support For Aws Security Hub Empowering Centralized Security Reporting
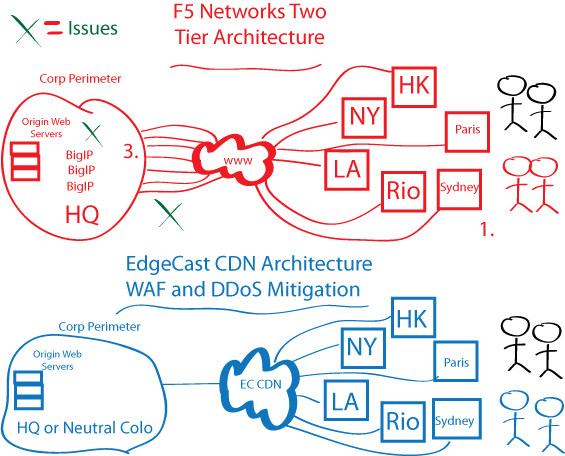
Edgecast Security Vs F5 Networks Bizety
Q Tbn And9gcsubusxdgaquj1w6ity46 Qncvb6qaqms7jx1ridy13b Keljll Usqp Cau

Awaf Orange Cyberdefense Belgium
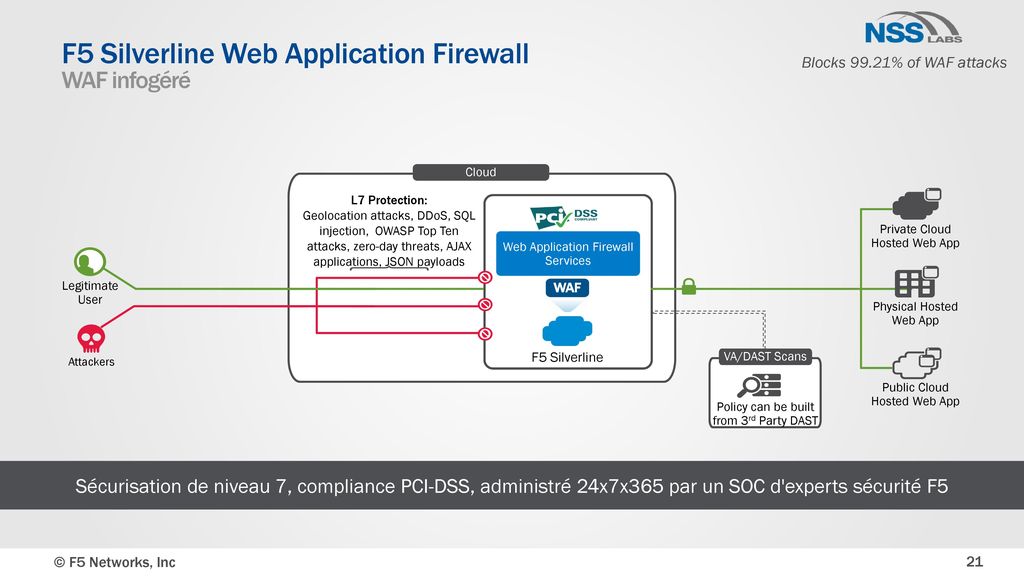
Presentation Offre F5 Amine Fergoug Ppt Download

Installing F5 Big Ip Adc For Anthos Clusters On Vmware Solutions
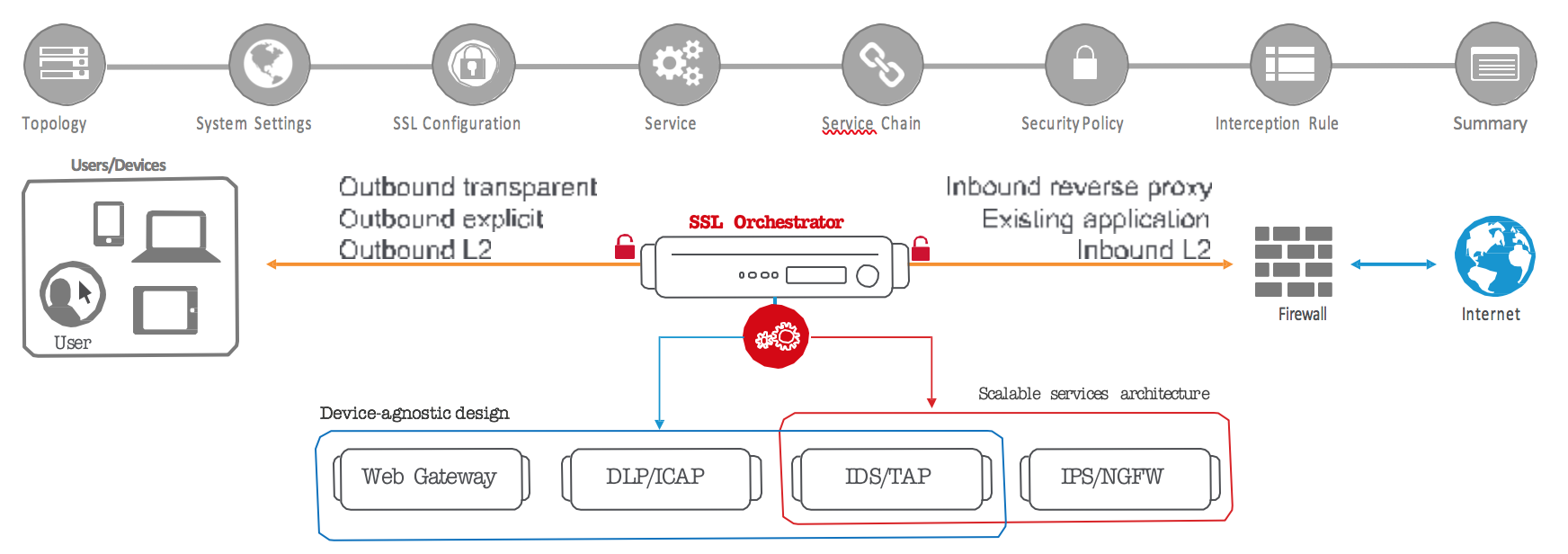
F5 Agility Labs Index

Waf Vs Ngfw

How To Enhance Your Application Security Strategy With F5 On Aws
Veracompadria Com Wp Content Uploads 17 02 Application Security Pdf

Aws Marketplace F5 Waf Solution 1gbps

Seguridad De La Informacion Redes Por David Romero Trejo
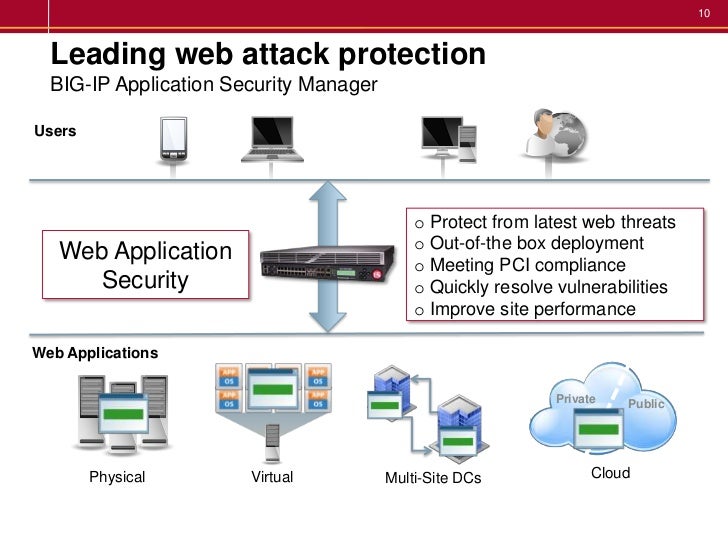
F5 Bigip Asm Introduction

Waf Vs Ips What S The Difference Lanner
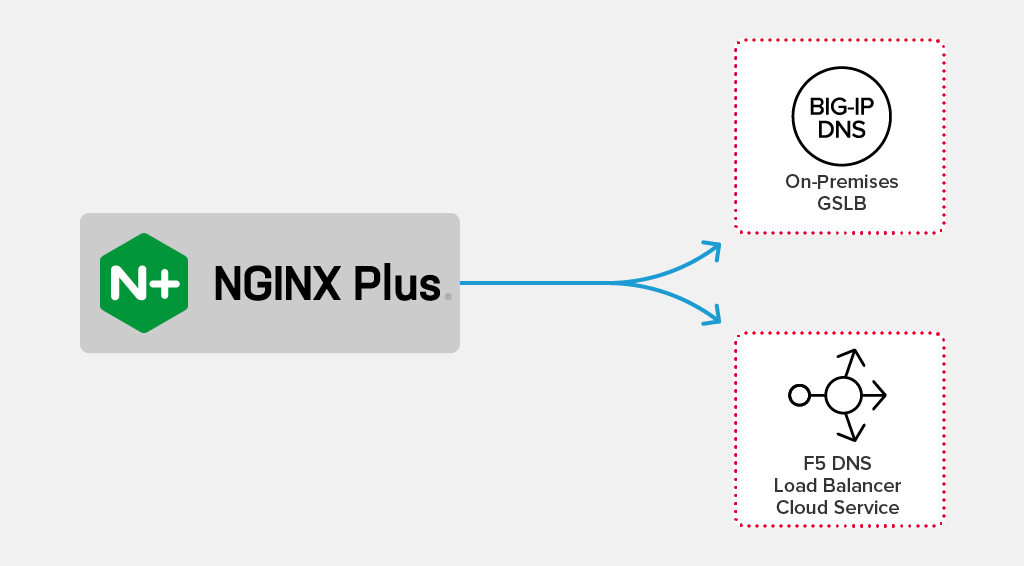
Just One Post Enabling Declarative Dns With F5 And The Nginx Javascript Module Nginx

Learn How To Detect And Block Threats Hidden In Ssl Streams

Stopping Layer 7 Attacks With F5 Asm Sven Muller Security Solution Architect Pdf Free Download
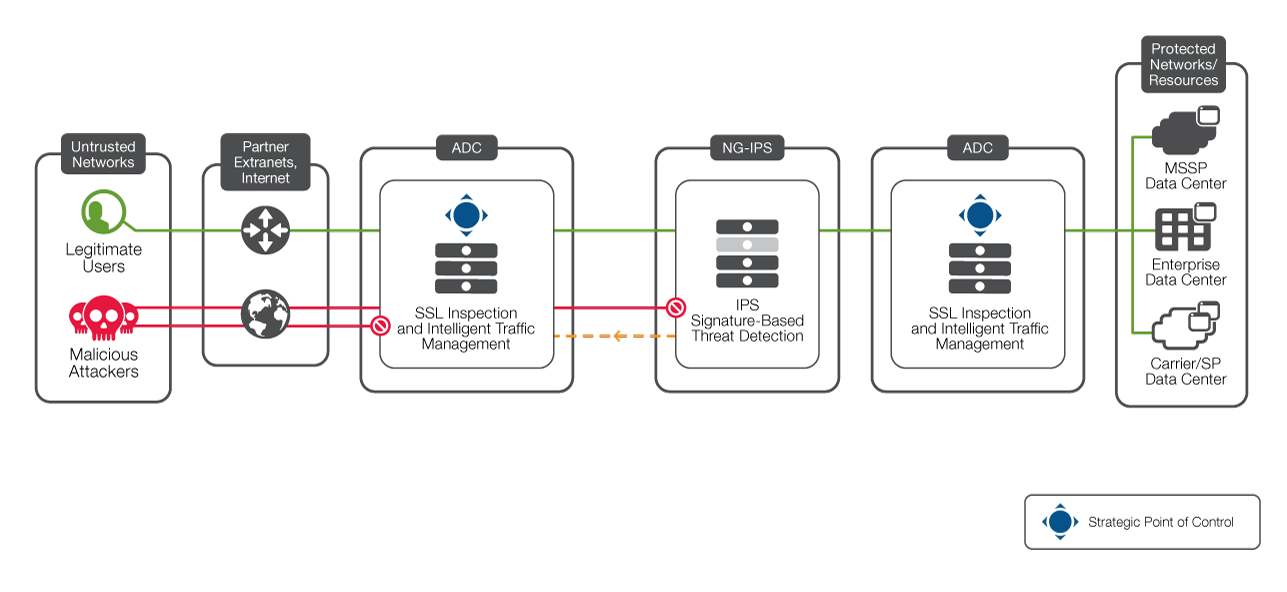
The F5 Ssl Reference Architecture

F5 Networks Wikipedia

F5 Secure Web Gateway Services Reference Architecture F5 White Pdf Document
Media Readthedocs Org Pdf F5 Agility Labs Waf Latest F5 Agility Labs Waf Pdf
Worldtechit Com Wp Content Uploads 15 07 F5 White Paper The F5 Ddos Protection Reference Architecture Pdf

Aws Api Gateway Protection With Big Ip Youtube

3 F5 Azure Scca Architecture

F5 Big Ip Reviews And Pricing It Central Station
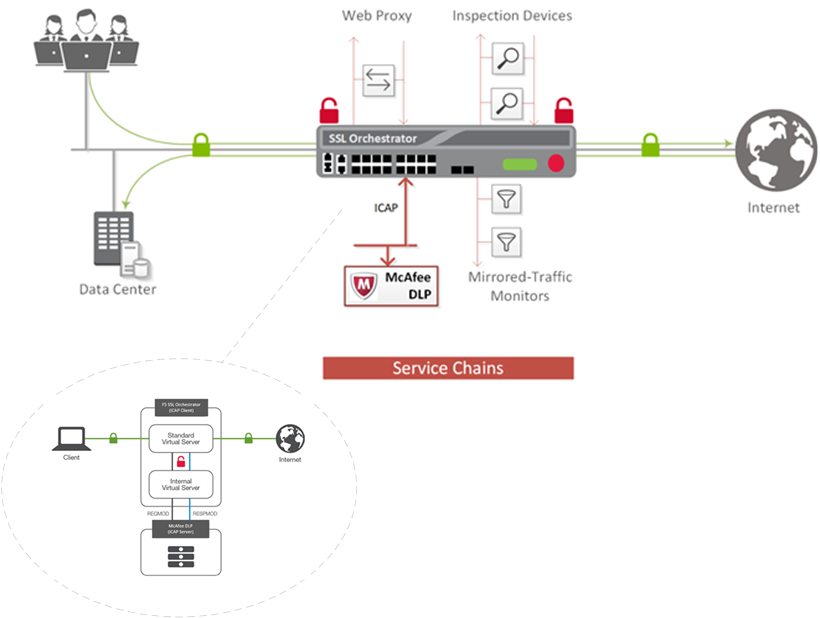
Matthieu Dierick Matt Dierick Twitter
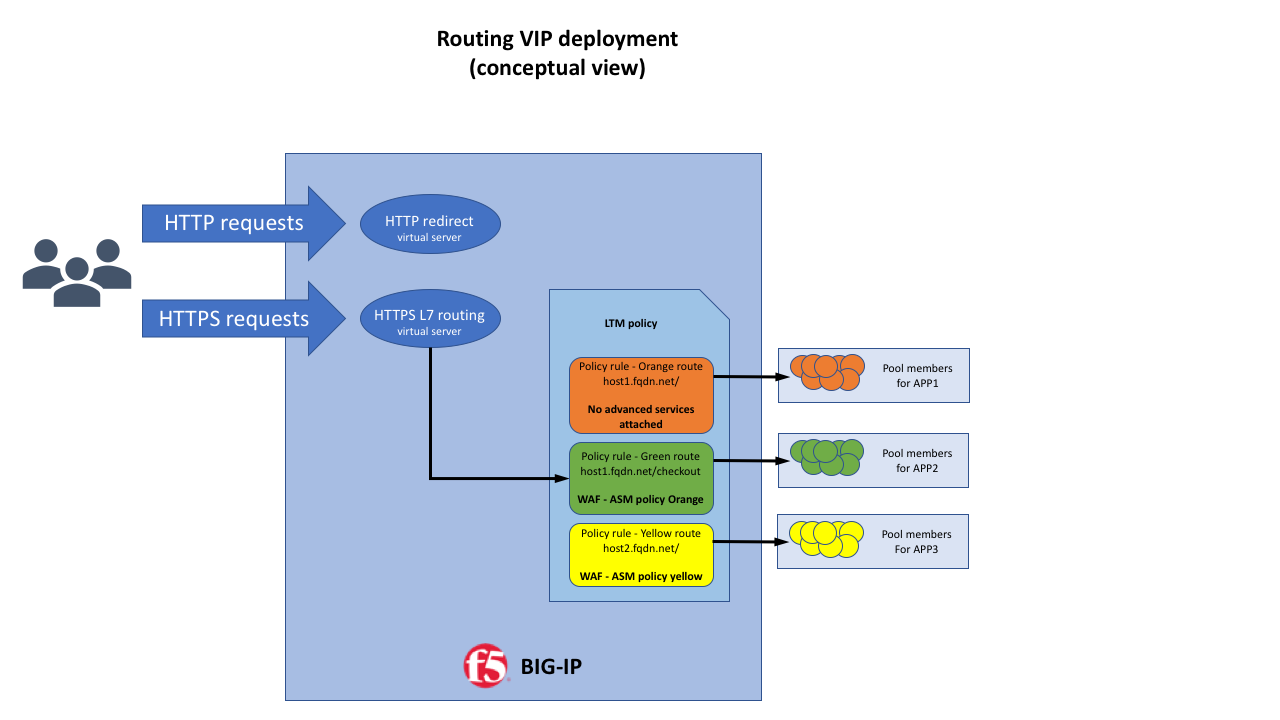
F5 Routing Vip Readme Md At Master F5devcentral F5 Routing Vip Github
Silverline Waf Architecture Devcentral
Ddos Architecture Diagrams And White Paper F5

F5 Big Ip Ve On Aws Quick Start

F5 Big Ip Cloud Edition More Flexibility For Your Apps Veracomp We Inspire It
Web Application Firewall 101 Learn All About Wafs

Deploy F5 Across Two Azure Stack Hub Instances Azure Stack Hub Microsoft Docs
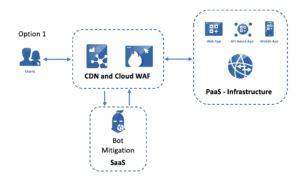
An Alternative Approach To Waap Architecture Cequence
Veracompadria Com Wp Content Uploads 17 02 Application Security Pdf
Silverline Waf Architecture Devcentral

Two Key Takeaways From F5 Agility Conference Knowledge Experience And Learning

Configuring Reverse Proxy Access To Microsoft Lync Using F5 Big Ip Local Traffic Manager Microsoft Tech Community

Tmg2f5 Series Publishing Microsoft Exchange Using F5 Networking In The Windows World
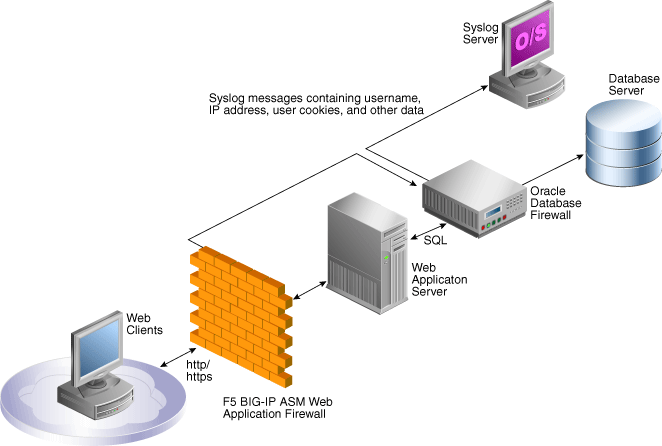
Using Oracle Database Firewall With Big Ip Asm
F5 Synthesis Delivering Web Application Security In The Cloud As A Service Devcentral
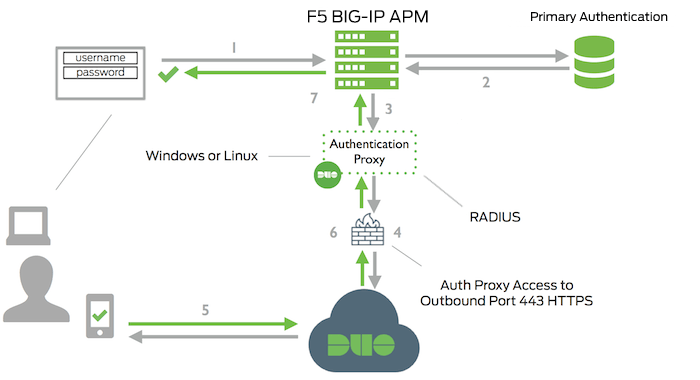
Two Factor Authentication For F5 Big Ip Apm With Radius And Duo Prompt Duo Security
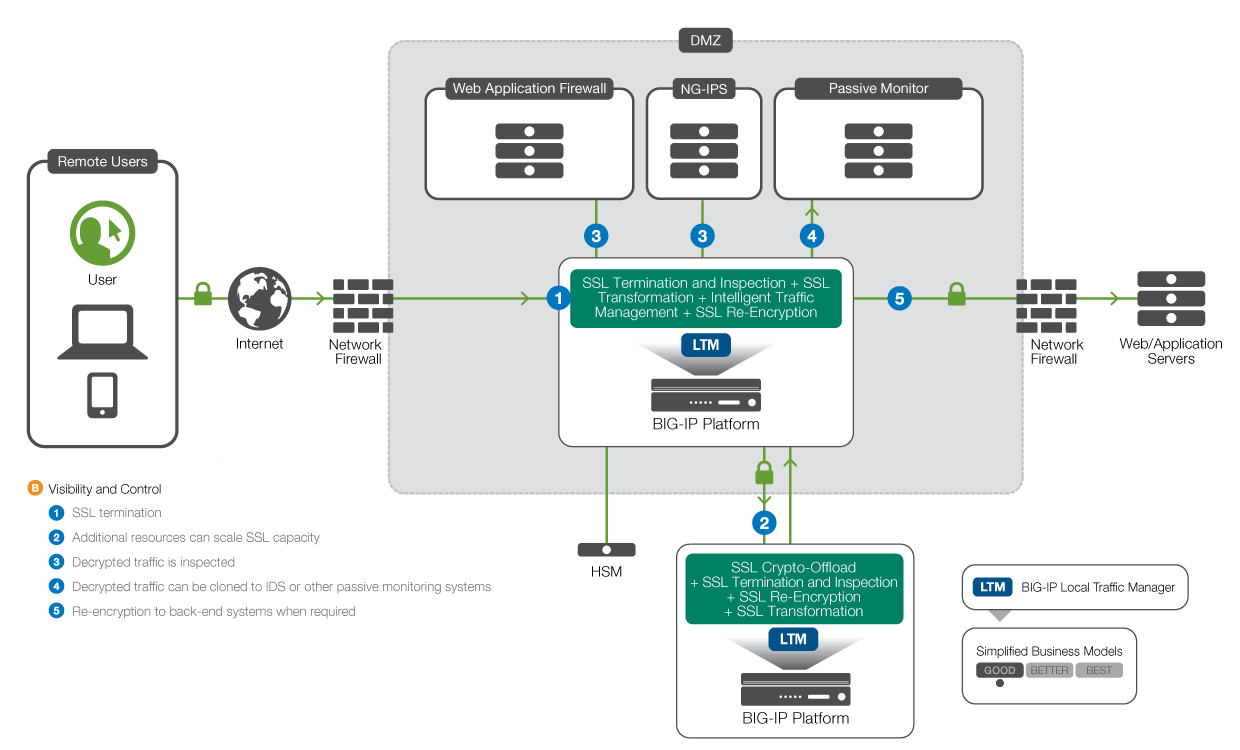
The F5 Ssl Reference Architecture

What The Heck Is F5 Networks Tmos Packet Pushers
Avi Networks Vs F5 Networks Avi Networks

Chunghwa Telecom Hicloud

Using F5 Big Ip As A Load Balancer For External Internet Connectivity
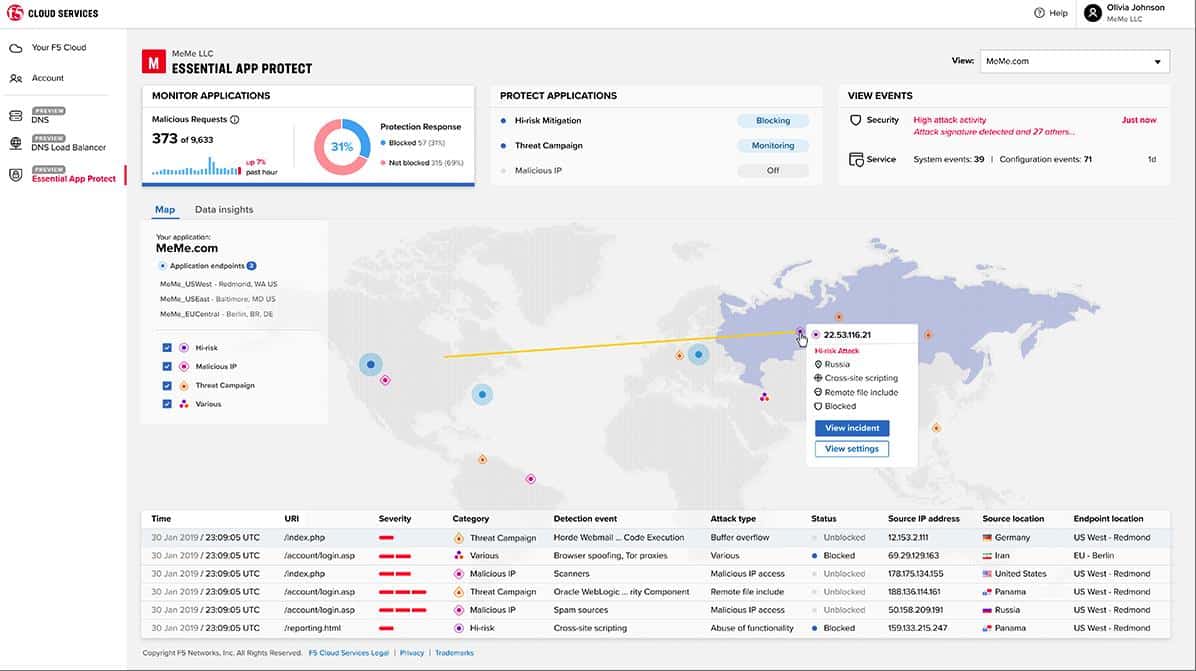
11 Best Web Application Firewalls Waf Buyer S Guide For 21

The F5 Ddos Protection Reference Architecture

Big Ip F5 Deployment Scenarios Youtube

Using F5 Big Ip As A Load Balancer For External Internet Connectivity

Introducing Nginx App Protect Advanced F5 Application Security For Nginx Plus Nginx
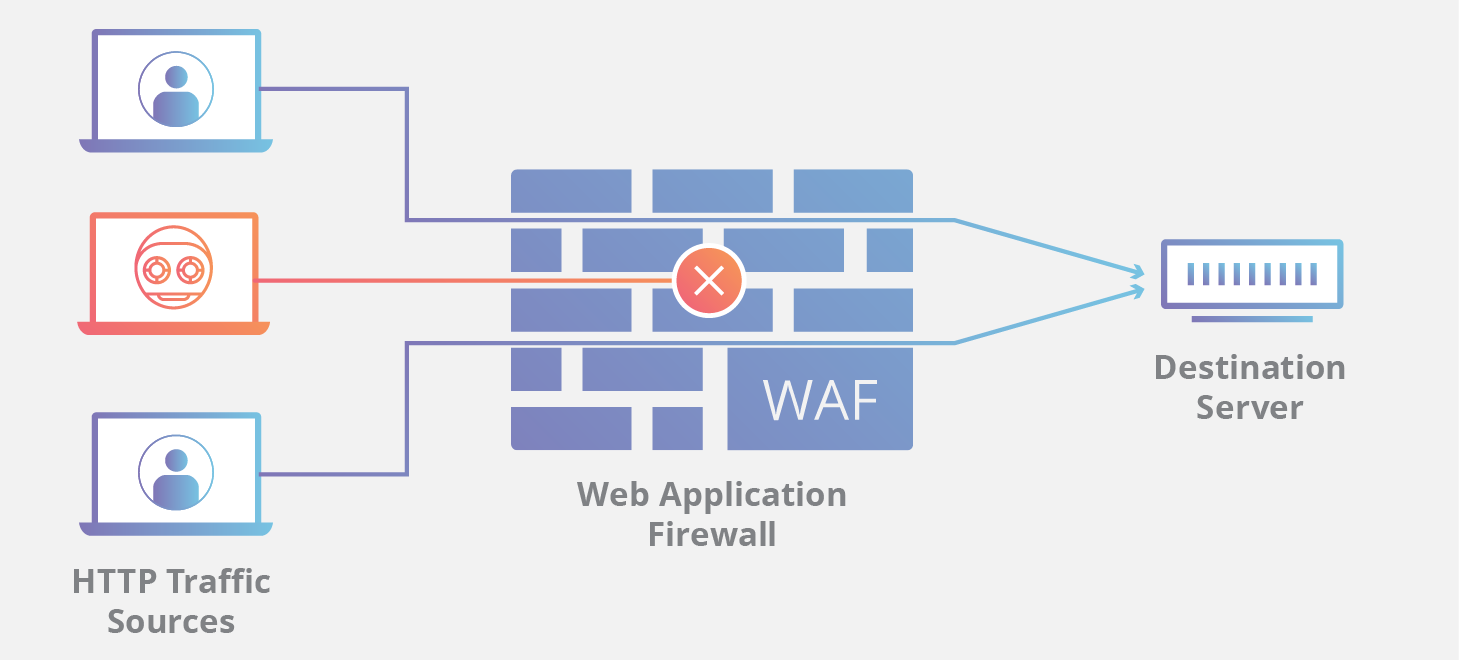
What Is A Waf Web Application Firewall Explained Cloudflare

Seguridad De La Informacion Redes Por David Romero Trejo

F5 Networks Web Application Firewall Waf Infradata
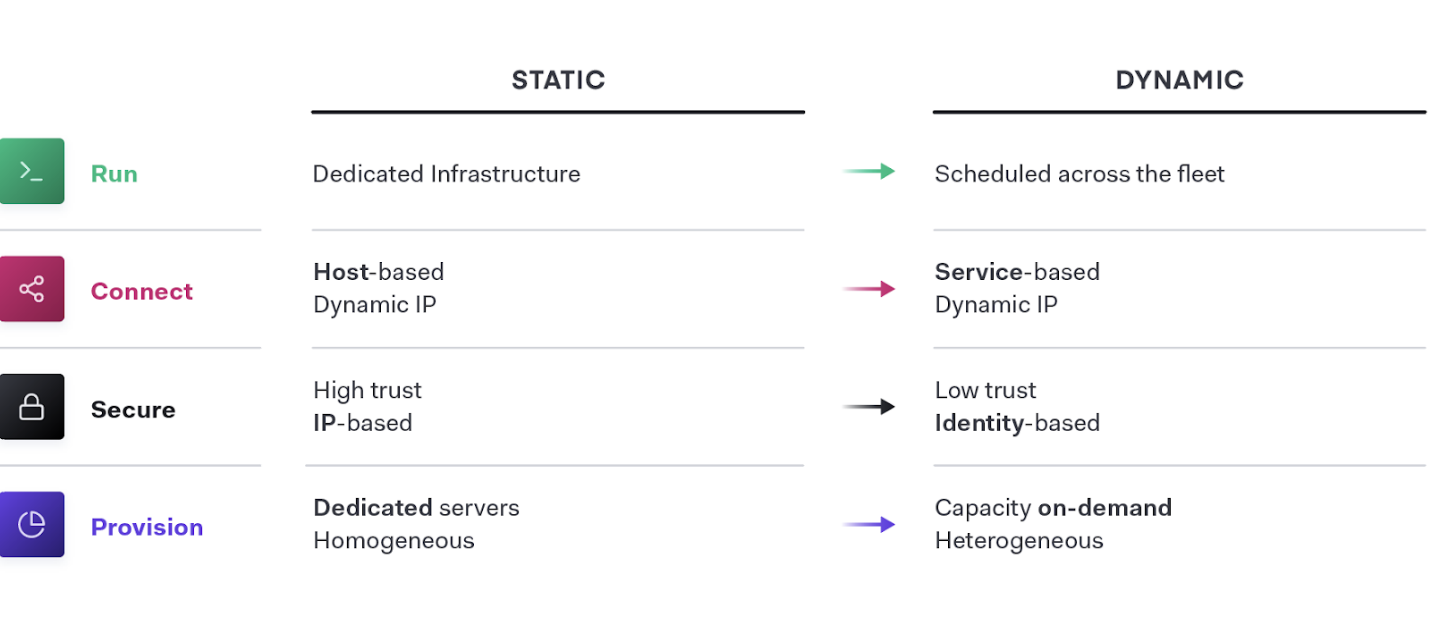
Automating Application Delivery In The Cloud Operating Model With F5
Load Balancer Refresh Avi Networks

F5 Ddos Protection

Article K What Is A Waf
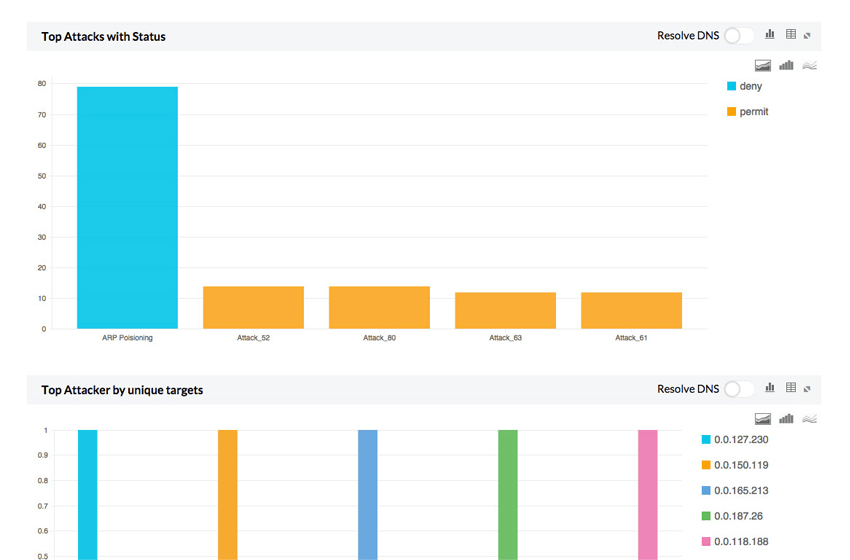
F5 Big Ip Firewall Logs F5 Big Ip Log Analyzer Manageengine

3 F5 Azure Scca Architecture
Worldtechit Com Wp Content Uploads 15 07 F5 White Paper The F5 Ddos Protection Reference Architecture Pdf
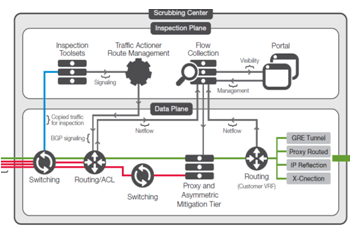
Individual Vendor Review F5 Red Button
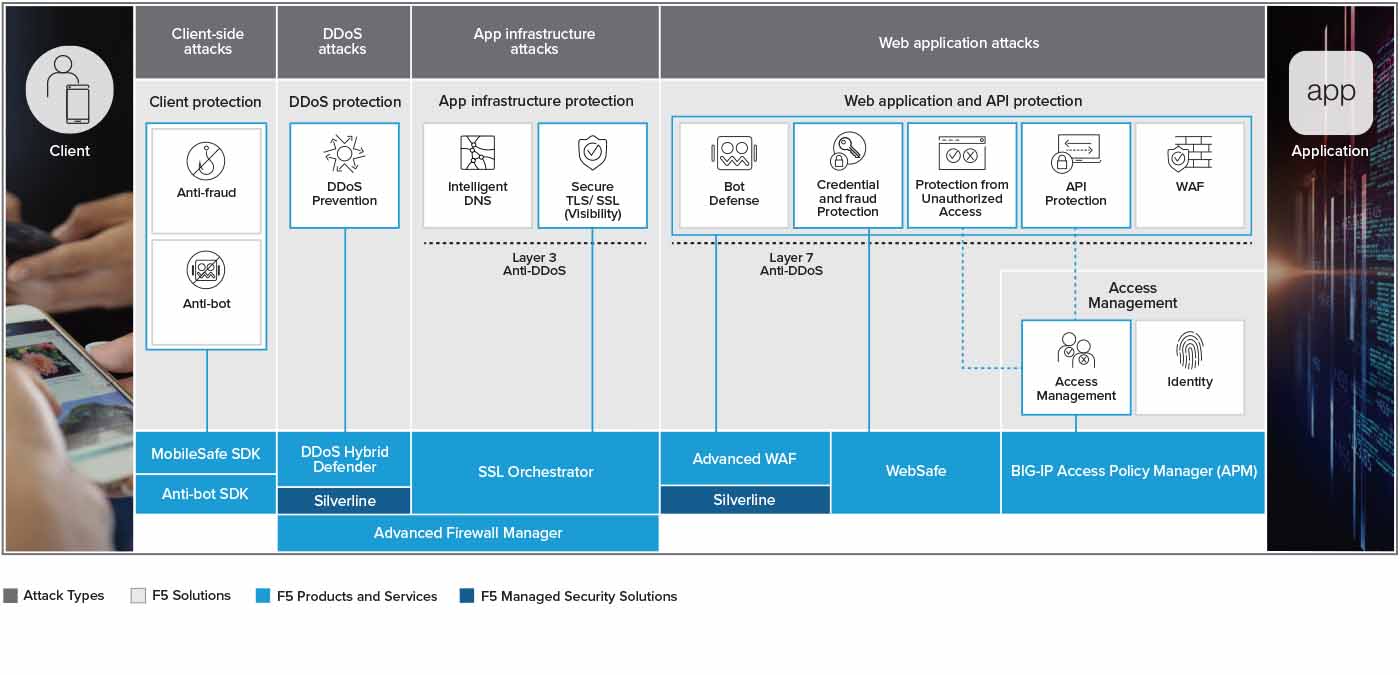
Idevnews F5 Updates End To End App Security With Optimized Ai And Broadened Portfolio
Www Alef Com Sk Na Stiahnutie F5 Silverline Web Application Firewall Dm 607 Pdf
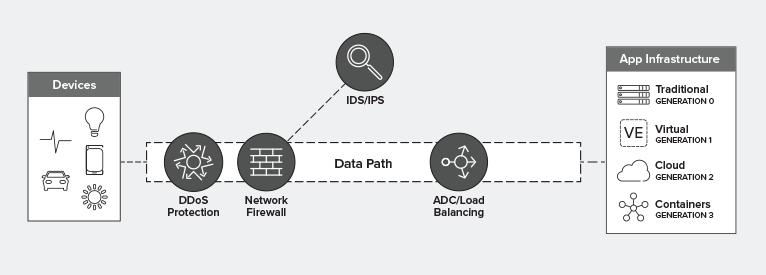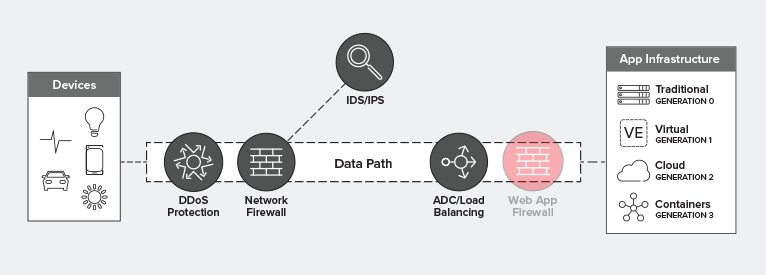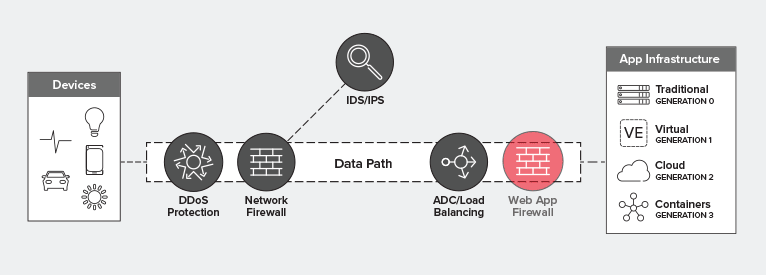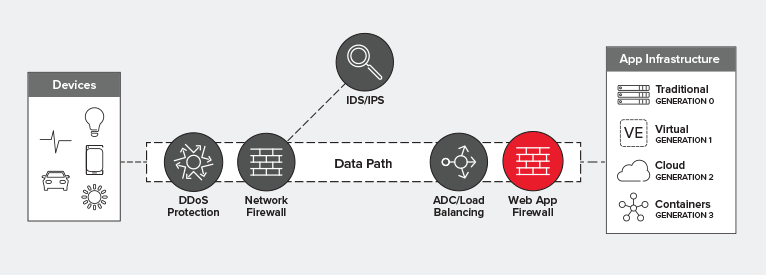
Where Does A Waf Fit In The Data Path F5

Tmg2f5 Series Publishing Microsoft Exchange Using F5 Networking In The Windows World
Q Tbn And9gcswqx6xxhyxp0sn Hsig Uck7yvyaxgghwwoyj Jrmo5cmlnx8m Usqp Cau

Installing F5 Big Ip Adc For Anthos Clusters On Vmware Using Manual Load Balancing
Www Ibm Com Cloud Garage Files Ibm Cloud For Vmware Solutions F5 Bigip Architecture Pdf
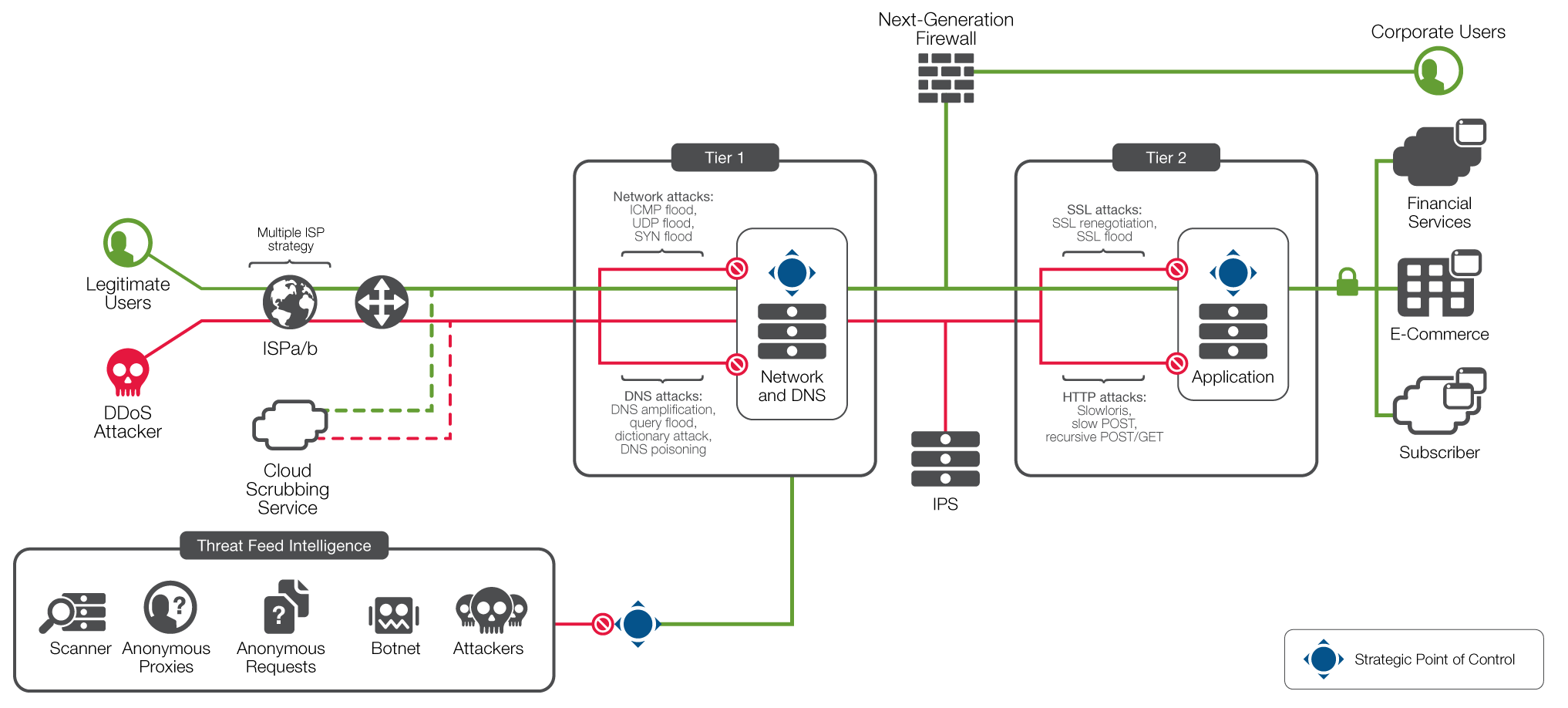
F5 Ddos Protection Recommended Practices Volume 1

F5 Silverline Web Application Firewall Onboarding Technical Note Pdf Free Download
M Softchoice Com Web Newsite Documents Amplify F5 Securing Your Customers Modern Cloud Journey Pdf
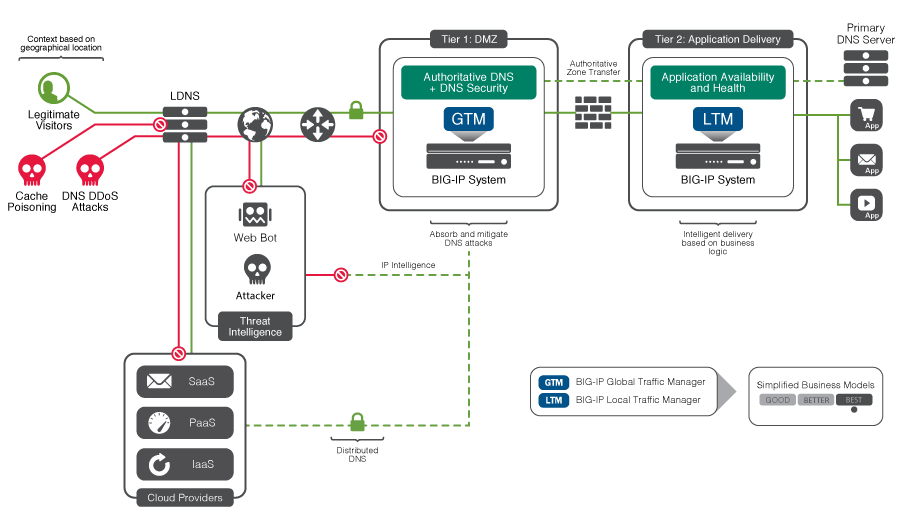
F5 Enterprise Solutions Application Delivery Appdeliveryworks Com

Simplicity And Security Through Centralized Application Delivery And F5 Networks Aws Partner Network Apn Blog

Web Application Firewall Akamai

Aws Marketplace Web Application Firewall
Www Veracomp Ro Wp Content Uploads 01 F5 Emea Product Guide Jan Public Pdf



